Welcome to PrintableAlphabet.net, your best resource for all points connected to What Are The Two Kinds Of Attacks In this extensive guide, we'll delve into the ins and outs of What Are The Two Kinds Of Attacks, giving beneficial understandings, involving tasks, and printable worksheets to boost your knowing experience.
Recognizing What Are The Two Kinds Of Attacks
In this area, we'll discover the basic concepts of What Are The Two Kinds Of Attacks. Whether you're a teacher, moms and dad, or learner, acquiring a strong understanding of What Are The Two Kinds Of Attacks is crucial for effective language acquisition. Expect insights, ideas, and real-world applications to make What Are The Two Kinds Of Attacks revived.
7 Different Kinds Of Asian Noodles You Should Know Asian Inspirations

What Are The Two Kinds Of Attacks
What are the 12 most common types of cyberattacks If you re a small or medium sized business get current stats and dive deeper into why your organization size can be at risk for cyberattacks 1 Malware or malicious
Discover the significance of grasping What Are The Two Kinds Of Attacks in the context of language development. We'll talk about just how proficiency in What Are The Two Kinds Of Attacks lays the structure for enhanced analysis, composing, and overall language skills. Explore the more comprehensive effect of What Are The Two Kinds Of Attacks on reliable interaction.
What Is Computer Security Kinds Of Attacks In CS Projectcubicle

What Is Computer Security Kinds Of Attacks In CS Projectcubicle
Mitigate the attack Use Firewalls Firewalls have simple rules such as to allow or deny protocols ports or IP addresses Modern stateful firewalls like Check Point FW1 NGX and Cisco PIX have a built in capability to differentiate good traffic
Knowing does not have to be boring. In this area, find a variety of appealing activities tailored to What Are The Two Kinds Of Attacks students of all ages. From interactive video games to creative exercises, these tasks are designed to make What Are The Two Kinds Of Attacks both fun and instructional.
What Are The Different Kinds Of Heart Attacks Extra Health Zone

What Are The Different Kinds Of Heart Attacks Extra Health Zone
Cyberattacks can fit into two categories insider threats or outsider threats Insider threats stem from individuals with legitimate access to the systems they target using their access to exploit vulnerabilities intentionally or
Access our particularly curated collection of printable worksheets concentrated on What Are The Two Kinds Of Attacks These worksheets satisfy various skill degrees, making sure a personalized understanding experience. Download, print, and take pleasure in hands-on tasks that strengthen What Are The Two Kinds Of Attacks skills in a reliable and satisfying way.
Types Of Noun
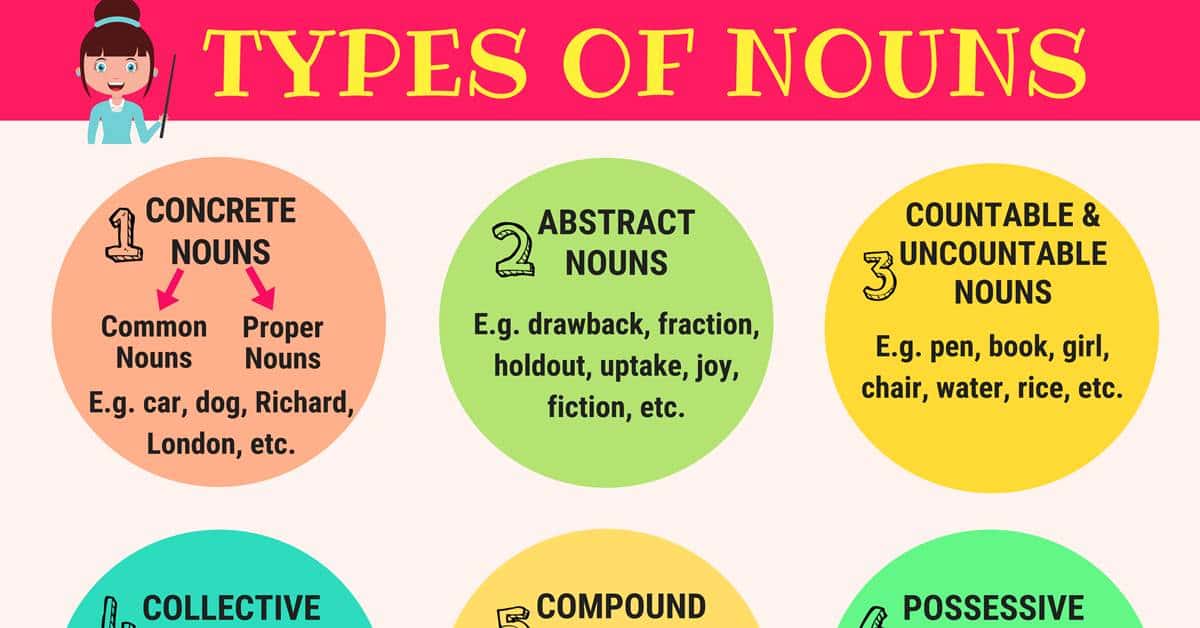
Types Of Noun
Here are the most damaging types of cyberattacks and what to do to prevent them Today s cybercriminals are not part time amateurs or script kiddies but rather state sponsored adversaries and professional criminals looking to
Whether you're an educator looking for efficient methods or a student looking for self-guided techniques, this area offers functional ideas for mastering What Are The Two Kinds Of Attacks. Take advantage of the experience and insights of educators that concentrate on What Are The Two Kinds Of Attacks education and learning.
Connect with similar people that share an interest for What Are The Two Kinds Of Attacks. Our community is an area for instructors, moms and dads, and students to trade ideas, inquire, and commemorate successes in the trip of understanding the alphabet. Sign up with the discussion and be a part of our growing neighborhood.
Download More What Are The Two Kinds Of Attacks








https://www.crowdstrike.com › ... › common …
What are the 12 most common types of cyberattacks If you re a small or medium sized business get current stats and dive deeper into why your organization size can be at risk for cyberattacks 1 Malware or malicious

https://eng.libretexts.org › Courses › Delta_…
Mitigate the attack Use Firewalls Firewalls have simple rules such as to allow or deny protocols ports or IP addresses Modern stateful firewalls like Check Point FW1 NGX and Cisco PIX have a built in capability to differentiate good traffic
What are the 12 most common types of cyberattacks If you re a small or medium sized business get current stats and dive deeper into why your organization size can be at risk for cyberattacks 1 Malware or malicious
Mitigate the attack Use Firewalls Firewalls have simple rules such as to allow or deny protocols ports or IP addresses Modern stateful firewalls like Check Point FW1 NGX and Cisco PIX have a built in capability to differentiate good traffic

Different Types Of Cyber Attack You Should Be Aware Off Riset

What Is The Most Common Type Of Security Attacks The Daily VPN

There Are Always Two Types Of People In The World YouTube

How To Make Salad Recipes Tips And More Taste Of Home

Noun Poster Teacha

Different Kinds Of Waterforms Lake River Ocean Strait Bay Pond

Different Kinds Of Waterforms Lake River Ocean Strait Bay Pond

What Are Several Different Groups Of Dog Breeds