Welcome to PrintableAlphabet.net, your go-to source for all points related to What Are The Types Of Threat In this detailed guide, we'll look into the details of What Are The Types Of Threat, supplying useful understandings, involving tasks, and printable worksheets to enhance your understanding experience.
Recognizing What Are The Types Of Threat
In this area, we'll explore the basic concepts of What Are The Types Of Threat. Whether you're an instructor, moms and dad, or student, obtaining a strong understanding of What Are The Types Of Threat is important for effective language procurement. Expect insights, pointers, and real-world applications to make What Are The Types Of Threat revived.
Insider Threat 4 Potential Threats To Your Business DeltalogiX

What Are The Types Of Threat
Learn about the different types of cyberattacks such as malware DoS phishing spoofing and more Find out how they work what they target and how to protect
Discover the importance of mastering What Are The Types Of Threat in the context of language growth. We'll review just how efficiency in What Are The Types Of Threat lays the structure for improved reading, composing, and total language abilities. Check out the broader effect of What Are The Types Of Threat on reliable interaction.
Meaning And Types Of Cybersecurity Threats INSIGHTSIAS

Meaning And Types Of Cybersecurity Threats INSIGHTSIAS
Malware short for malicious software is software code that is written intentionally to harm a computer system or its users Almost every modern cyberattack involves some
Knowing does not have to be dull. In this section, find a range of engaging tasks tailored to What Are The Types Of Threat students of any ages. From interactive video games to imaginative exercises, these tasks are created to make What Are The Types Of Threat both enjoyable and instructional.
Types Of Cyber Security Threats

Types Of Cyber Security Threats
Learn about the various types of cyberattacks organizations face today and how you can guard against them to keep yourself your information and your business safer The article covers malware
Access our particularly curated collection of printable worksheets focused on What Are The Types Of Threat These worksheets cater to various skill levels, making sure a tailored discovering experience. Download and install, print, and appreciate hands-on tasks that strengthen What Are The Types Of Threat skills in an effective and delightful way.
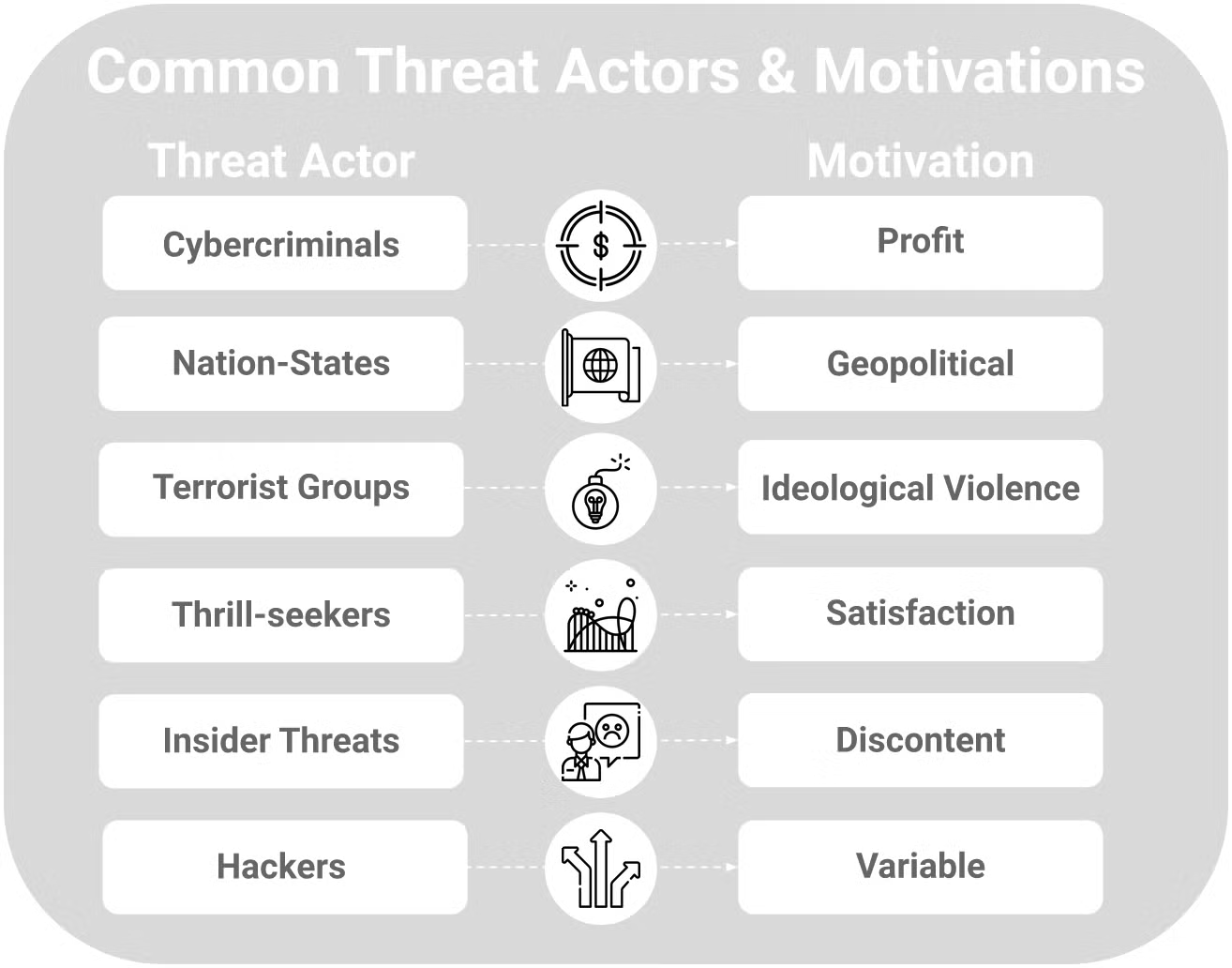
Threat Actor Basics Understanding The 5 Main Threat Types Phoenix

Threat Actor Basics Understanding The 5 Main Threat Types Phoenix
Common categories of cyber threats include malware social engineering man in the middle MitM attacks denial of service DoS and injection attacks we describe each of these categories in
Whether you're an instructor looking for reliable approaches or a student looking for self-guided approaches, this area supplies useful suggestions for understanding What Are The Types Of Threat. Benefit from the experience and insights of instructors that concentrate on What Are The Types Of Threat education.
Get in touch with like-minded people who share a passion for What Are The Types Of Threat. Our community is a space for instructors, parents, and learners to exchange ideas, inquire, and commemorate successes in the journey of understanding the alphabet. Join the conversation and belong of our expanding area.
Here are the What Are The Types Of Threat





https://www.crowdstrike.com/cybersecurity-101/...
Learn about the different types of cyberattacks such as malware DoS phishing spoofing and more Find out how they work what they target and how to protect

https://www.ibm.com/think/topics/cyberthreats-types
Malware short for malicious software is software code that is written intentionally to harm a computer system or its users Almost every modern cyberattack involves some
Learn about the different types of cyberattacks such as malware DoS phishing spoofing and more Find out how they work what they target and how to protect
Malware short for malicious software is software code that is written intentionally to harm a computer system or its users Almost every modern cyberattack involves some

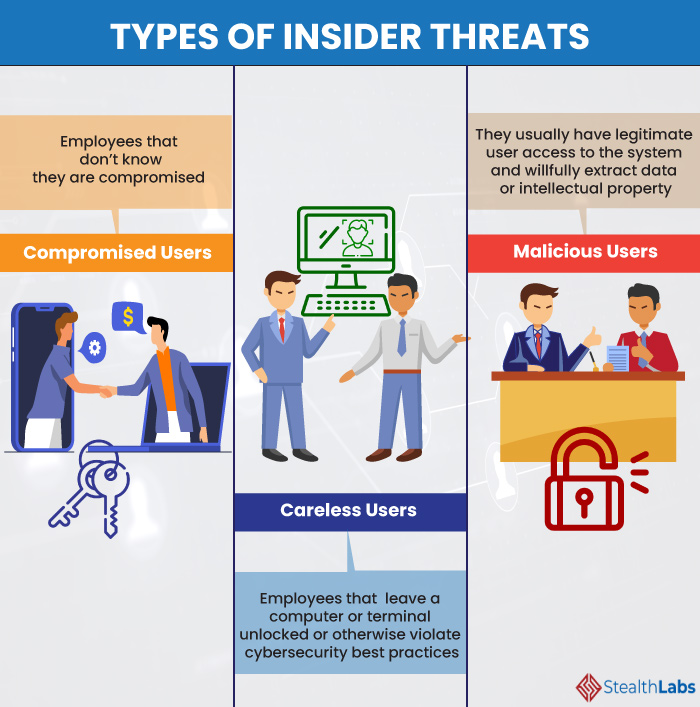
Your Security Guide To Insider Threats Detection Best Practices

Threat Levels ProtectUK

How To Mitigate Insider Threats

Threat Modeling The Why How When And Which Tools DevOps
Principles

What Are The Types Of Threats

What Are The Types Of Threats
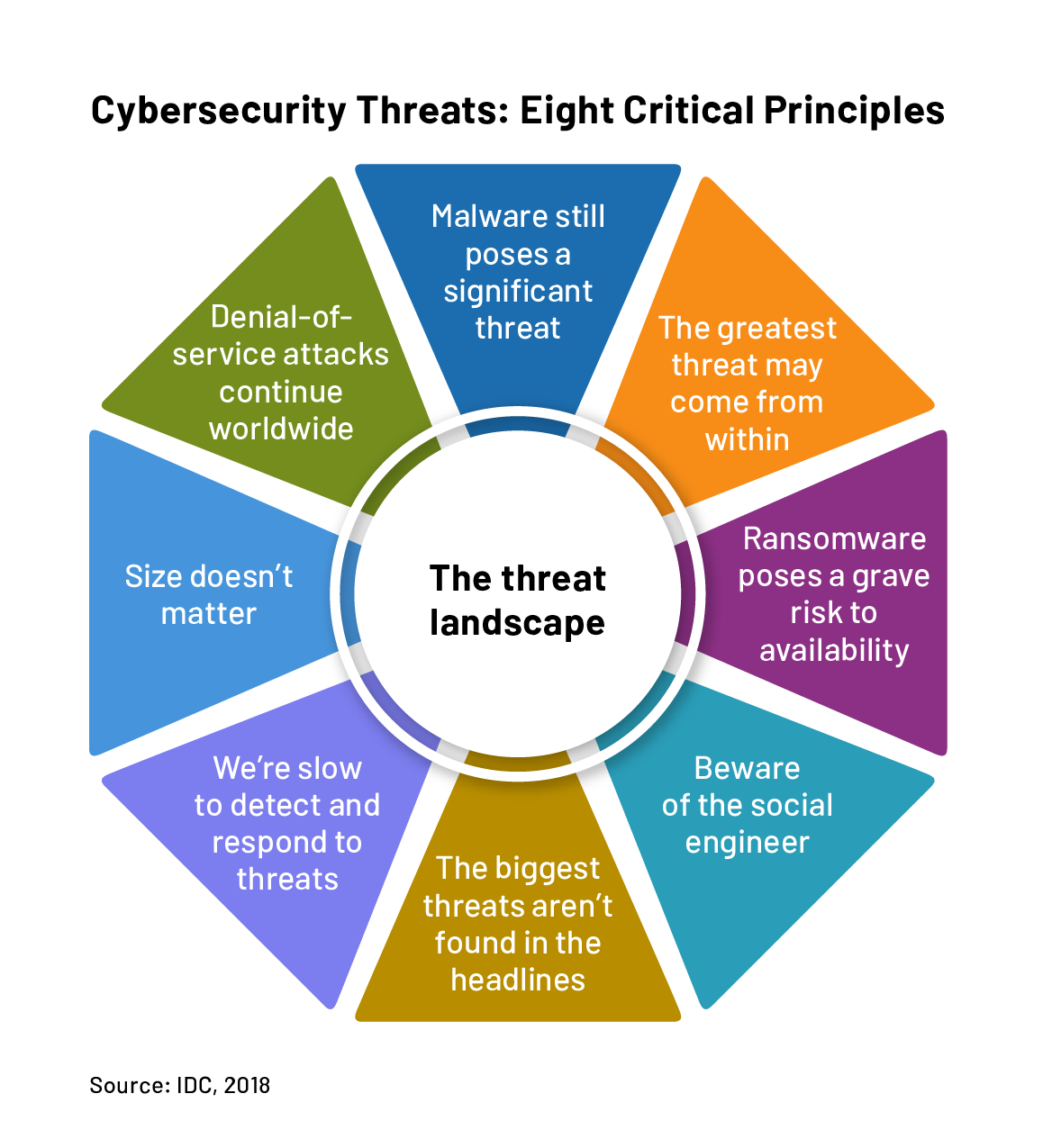
Cybersecurity Threats Eight Things CIOs Need To Know Dome9