Invite to Our blog, an area where interest meets info, and where day-to-day subjects come to be interesting discussions. Whether you're looking for understandings on way of living, technology, or a little bit of whatever in between, you have actually landed in the appropriate place. Join us on this exploration as we dive into the realms of the common and extraordinary, understanding the globe one post at a time. Your journey into the remarkable and diverse landscape of our What Is Another Name For Man In The Middle Attack starts below. Explore the fascinating material that awaits in our What Is Another Name For Man In The Middle Attack, where we decipher the ins and outs of various subjects.
What Is Another Name For Man In The Middle Attack
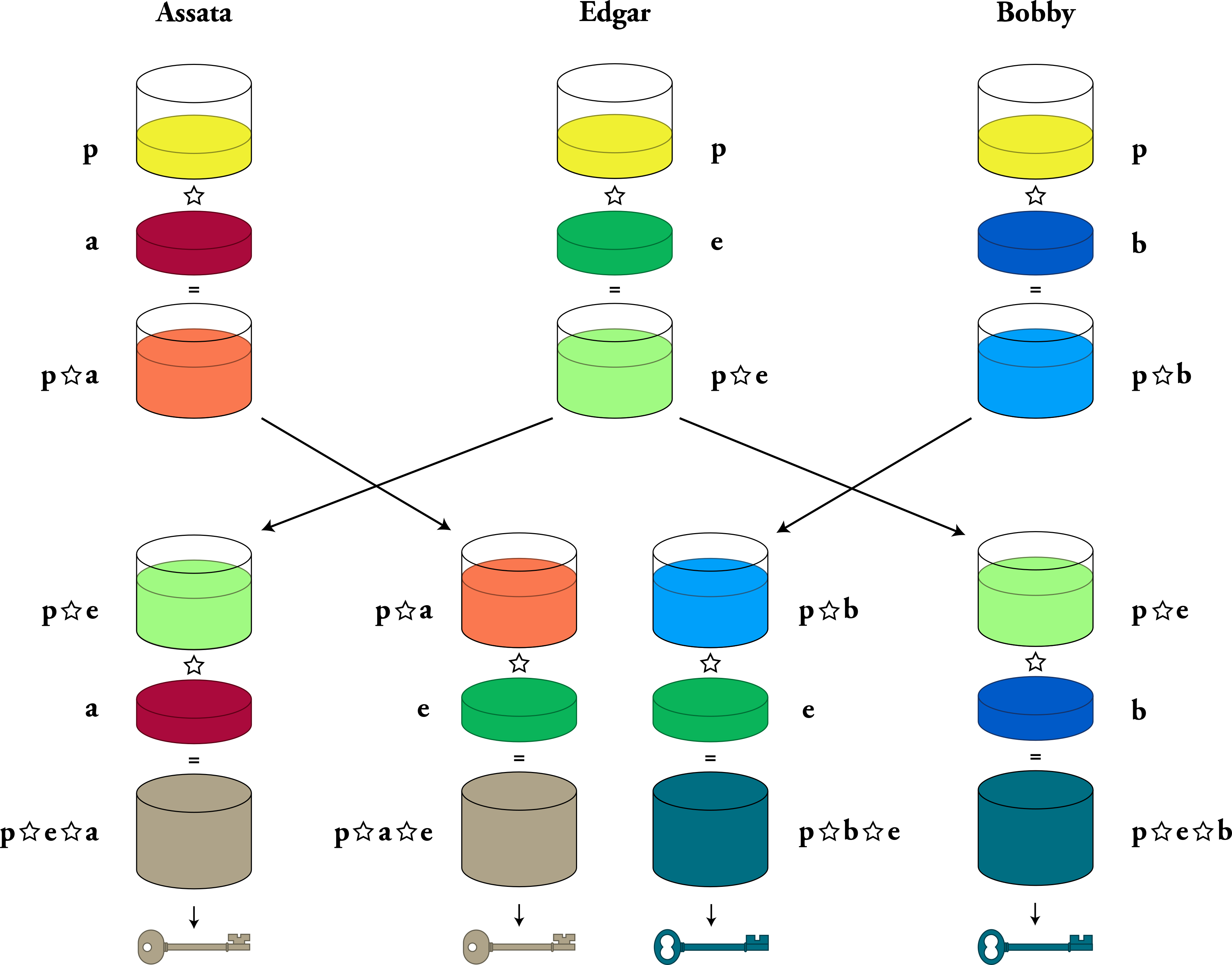
What Is Another Name For Man In The Middle Attack
Man In The Middle CapTex Bank
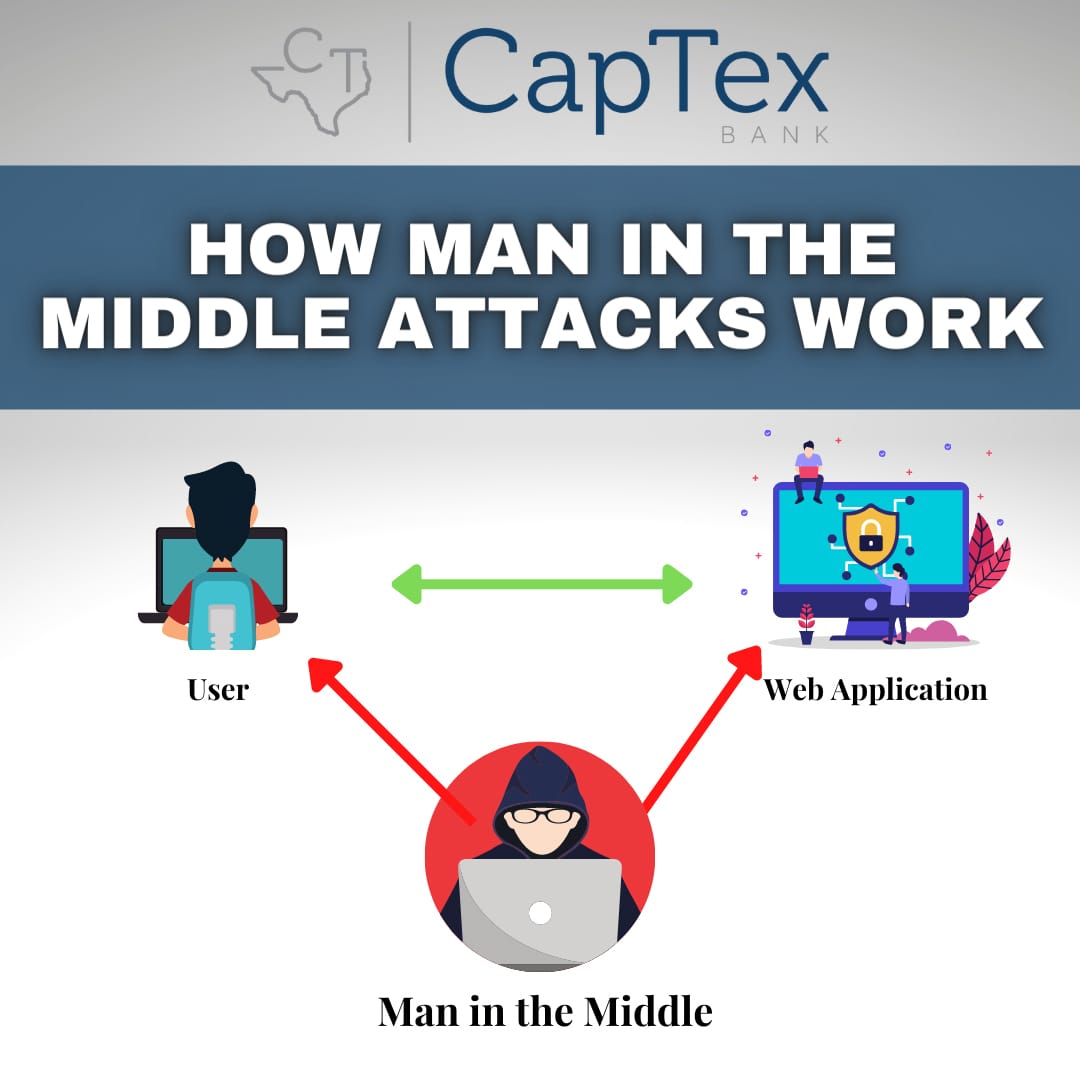
Man In The Middle CapTex Bank
Man In The Middle Attack Different Types And Techniques CYBERVIE

Man In The Middle Attack Different Types And Techniques CYBERVIE
Gallery Image for What Is Another Name For Man In The Middle Attack

What Is A Man in the Middle Attack MitM Attack Example Prevention

Man in the Middle Attacks How To Prevent Security Breaches
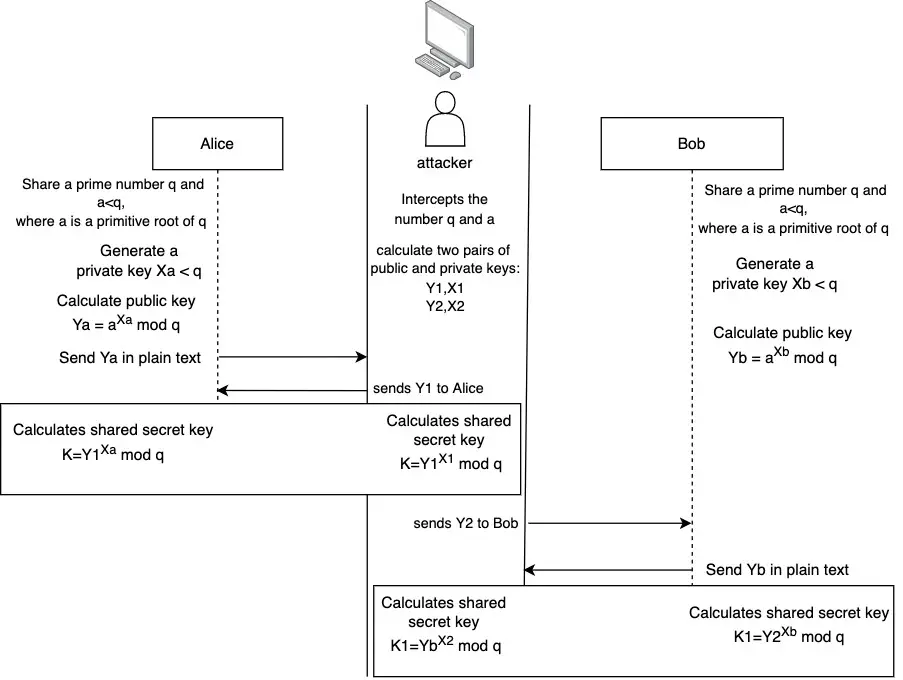
What Is The Man In The Middle Attack Just Cryptography

Mewaspadai Man In The Middle Attack Dan Cara Mengatasinya

Man in the Middle Attack Prevention Strategies For Financial Institutions

MITM Attacks Man In The Middle Attacks By CI T Australia CI T

MITM Attacks Man In The Middle Attacks By CI T Australia CI T

Is HTTPS The Answer To Man In The Middle Attacks
Thank you for picking to discover our web site. We best regards wish your experience exceeds your assumptions, and that you uncover all the details and sources about What Is Another Name For Man In The Middle Attack that you are looking for. Our dedication is to give a straightforward and useful platform, so feel free to navigate with our pages effortlessly.