Welcome to PrintableAlphabet.net, your go-to source for all points related to What Is Zero Trust Architecture In this thorough guide, we'll look into the intricacies of What Is Zero Trust Architecture, providing valuable understandings, involving activities, and printable worksheets to improve your knowing experience.
Recognizing What Is Zero Trust Architecture
In this section, we'll check out the essential ideas of What Is Zero Trust Architecture. Whether you're an educator, moms and dad, or learner, obtaining a strong understanding of What Is Zero Trust Architecture is crucial for effective language acquisition. Anticipate insights, pointers, and real-world applications to make What Is Zero Trust Architecture revived.
Zero Trust El Modelo De Ciberseguridad Que Est Cambiando El Paradigma

What Is Zero Trust Architecture
Zero Trust Architecture ZTA is a security model based on the principle of least privilege Least privilege means that users and devices are only granted the permissions they need to perform their tasks
Discover the significance of grasping What Is Zero Trust Architecture in the context of language growth. We'll go over how efficiency in What Is Zero Trust Architecture lays the structure for improved reading, composing, and total language skills. Explore the wider effect of What Is Zero Trust Architecture on efficient communication.
Zero Trust Architecture What It Is And What I Think Of It Tristan
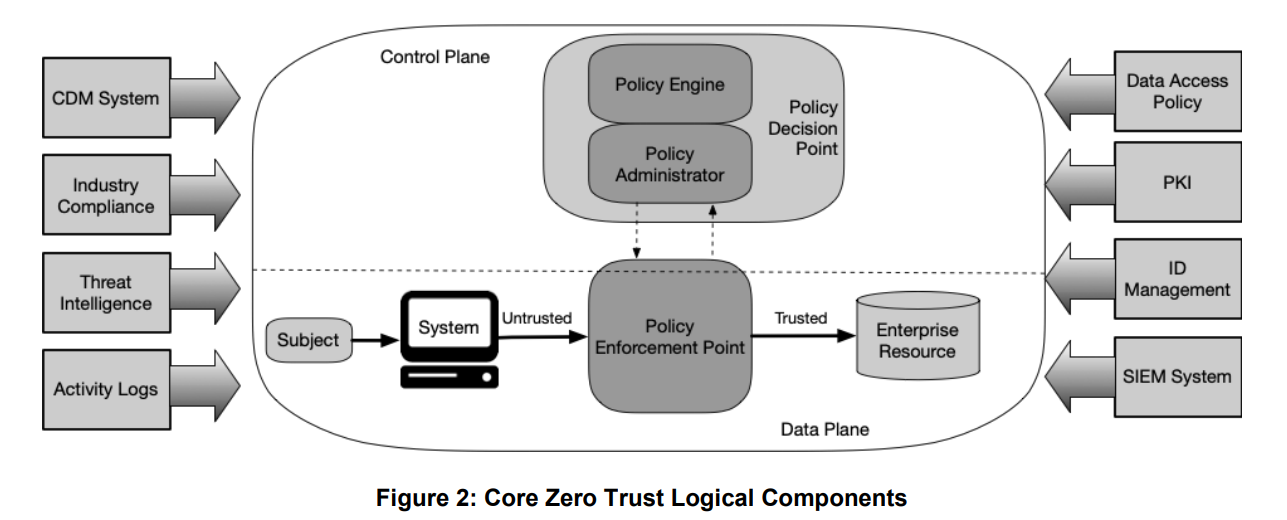
Zero Trust Architecture What It Is And What I Think Of It Tristan
A Zero Trust Architecture refers to the way network devices and services are structured to enable a Zero Trust security model
Knowing doesn't need to be plain. In this area, locate a variety of engaging activities customized to What Is Zero Trust Architecture students of all ages. From interactive games to imaginative workouts, these tasks are developed to make What Is Zero Trust Architecture both fun and academic.
Fakecineaste Zero Trust Architecture
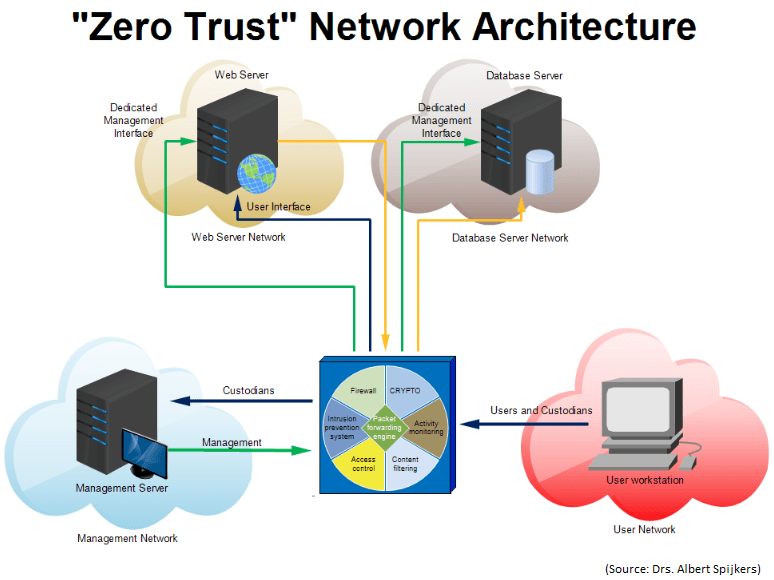
Fakecineaste Zero Trust Architecture
Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows
Accessibility our particularly curated collection of printable worksheets concentrated on What Is Zero Trust Architecture These worksheets deal with various ability levels, making sure a personalized knowing experience. Download, print, and delight in hands-on activities that enhance What Is Zero Trust Architecture abilities in an effective and delightful way.
Microsoft 365 Microsoft Learn

Microsoft 365 Microsoft Learn
A zero trust architecture ZTA is an enterprise s cyber security plan that utilizes zero trust concepts and encompasses component relationships workflow planning and access policies
Whether you're an instructor seeking efficient strategies or a learner seeking self-guided approaches, this section uses practical suggestions for grasping What Is Zero Trust Architecture. Gain from the experience and understandings of educators that concentrate on What Is Zero Trust Architecture education and learning.
Get in touch with similar individuals that share a passion for What Is Zero Trust Architecture. Our area is a space for educators, moms and dads, and learners to trade concepts, seek advice, and commemorate successes in the trip of grasping the alphabet. Sign up with the discussion and belong of our expanding neighborhood.
Here are the What Is Zero Trust Architecture
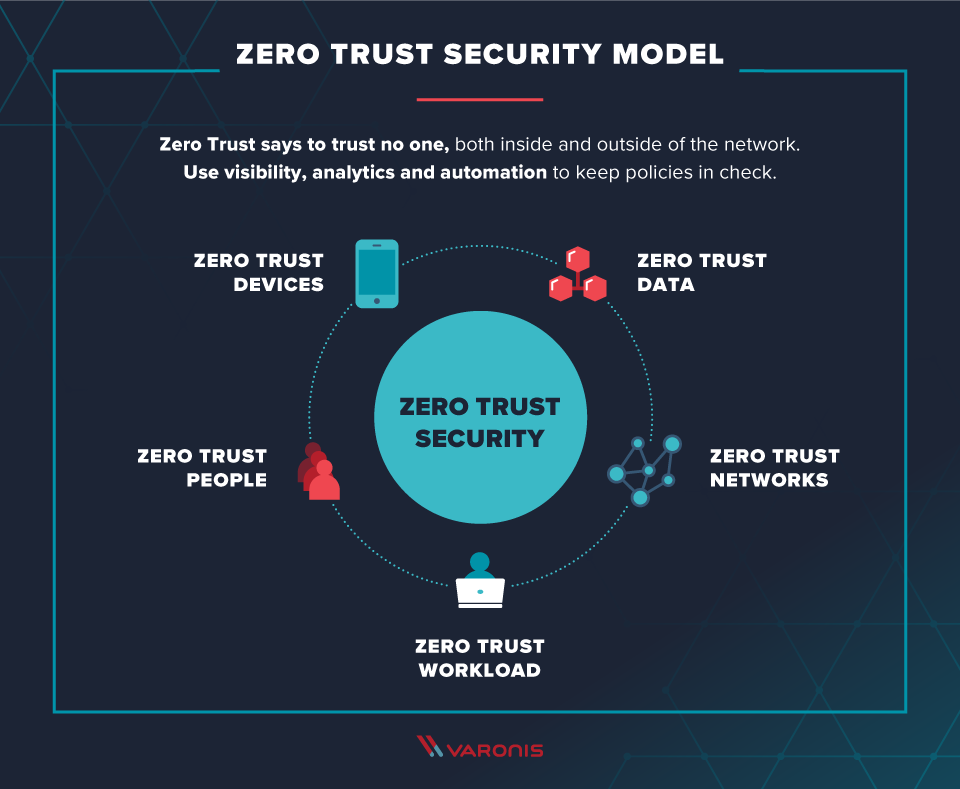


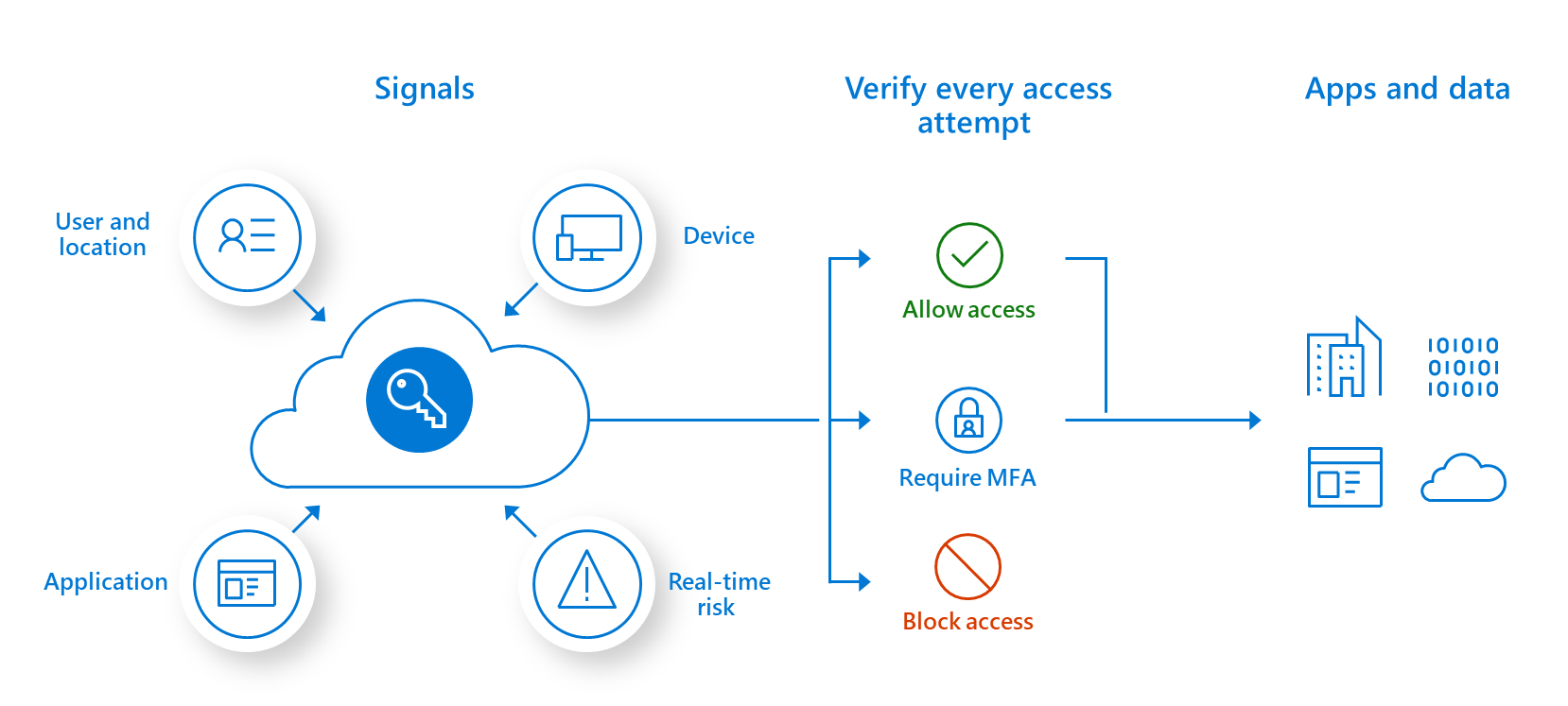
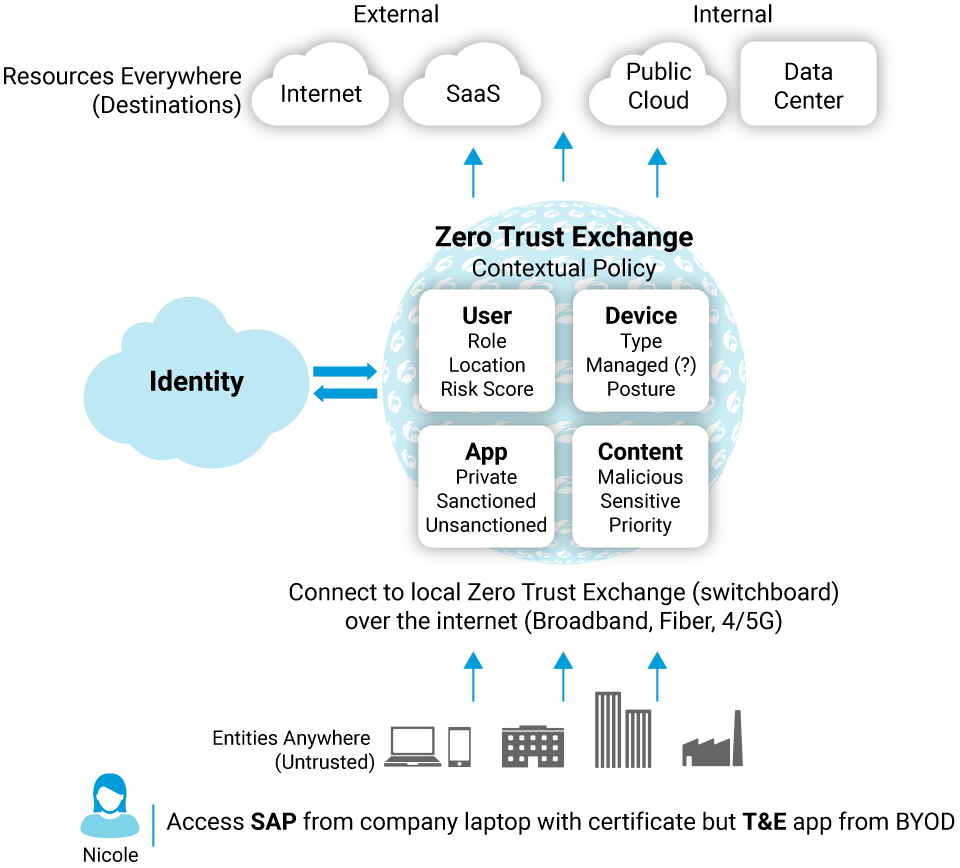
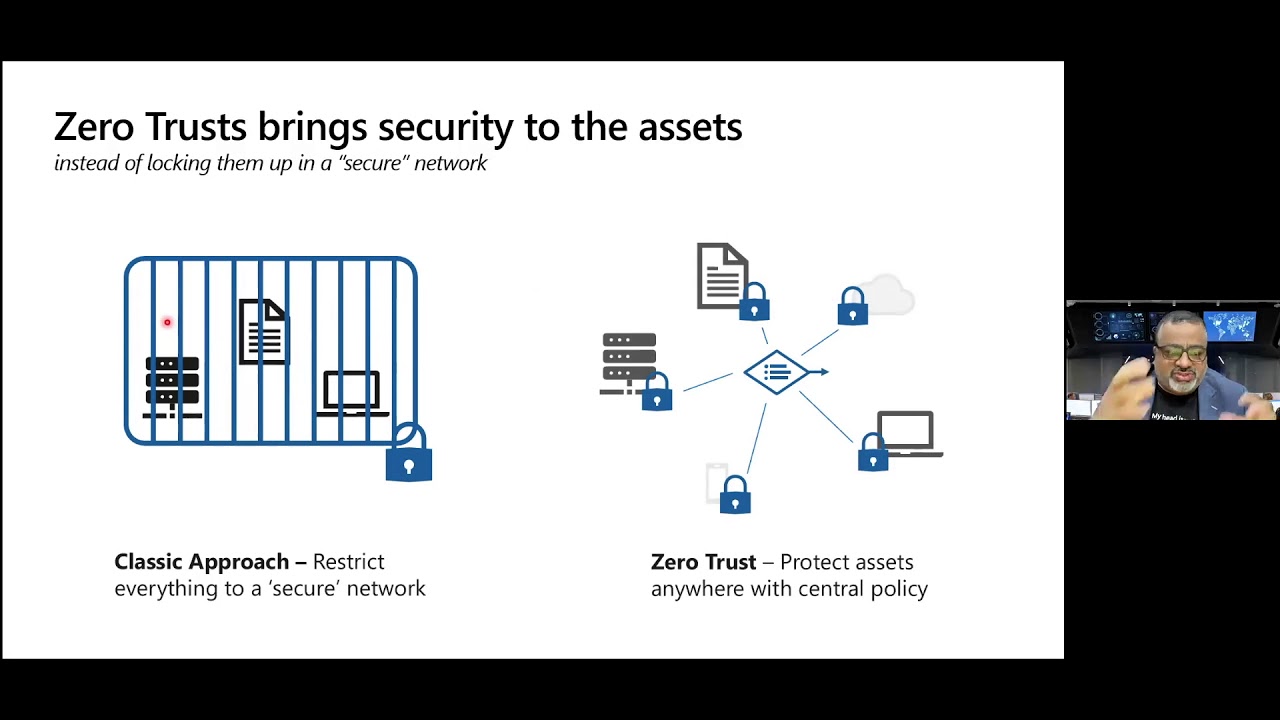


https://www.sans.org › blog › what-is-zero-trust-architecture
Zero Trust Architecture ZTA is a security model based on the principle of least privilege Least privilege means that users and devices are only granted the permissions they need to perform their tasks

https://www.crowdstrike.com › zero...
A Zero Trust Architecture refers to the way network devices and services are structured to enable a Zero Trust security model
Zero Trust Architecture ZTA is a security model based on the principle of least privilege Least privilege means that users and devices are only granted the permissions they need to perform their tasks
A Zero Trust Architecture refers to the way network devices and services are structured to enable a Zero Trust security model

Zero Trust Security Architecture

Zero Trust

Zero Trust Network Architecture Microsoft Case Study YouTube

How Fyde Implements Zero Trust To Enhance Security And Productivity
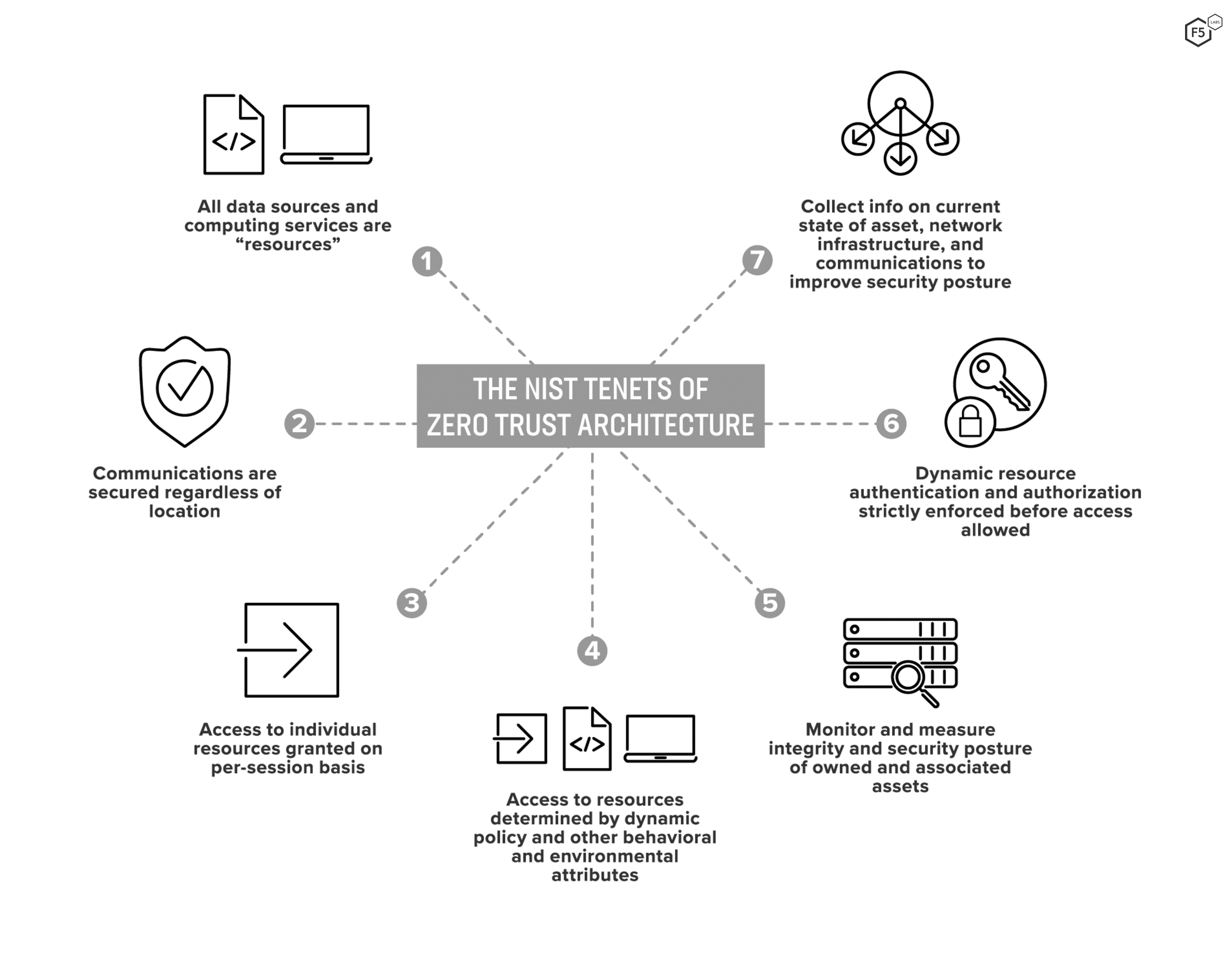
What Is Zero Trust Architecture ZTA F5 Labs

Terminalworks Blog Zero Trust Architecture

Terminalworks Blog Zero Trust Architecture
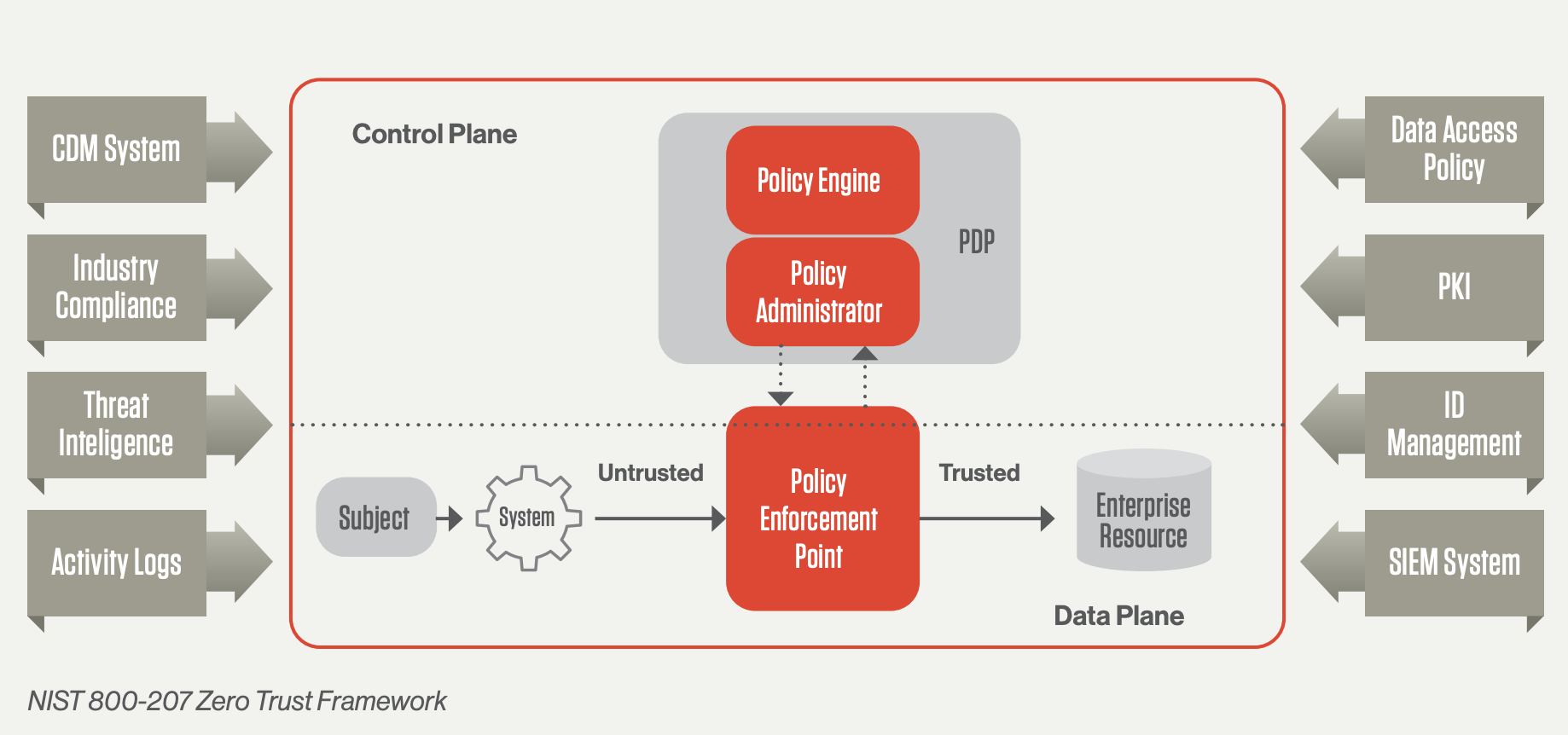
What Is Zero Trust Security Principles Of The Zero Trust Model