Welcome to PrintableAlphabet.net, your go-to source for all things associated with What Is Zero Trust Framework In this thorough overview, we'll delve into the ins and outs of What Is Zero Trust Framework, offering beneficial insights, involving tasks, and printable worksheets to boost your discovering experience.
Recognizing What Is Zero Trust Framework
In this section, we'll discover the fundamental principles of What Is Zero Trust Framework. Whether you're an instructor, moms and dad, or student, gaining a strong understanding of What Is Zero Trust Framework is crucial for successful language purchase. Anticipate insights, suggestions, and real-world applications to make What Is Zero Trust Framework revived.
What Is Zero Trust By Wentz Wu CISSP ISSMP ISSAP ISSEP CCSP CSSLP

What Is Zero Trust Framework
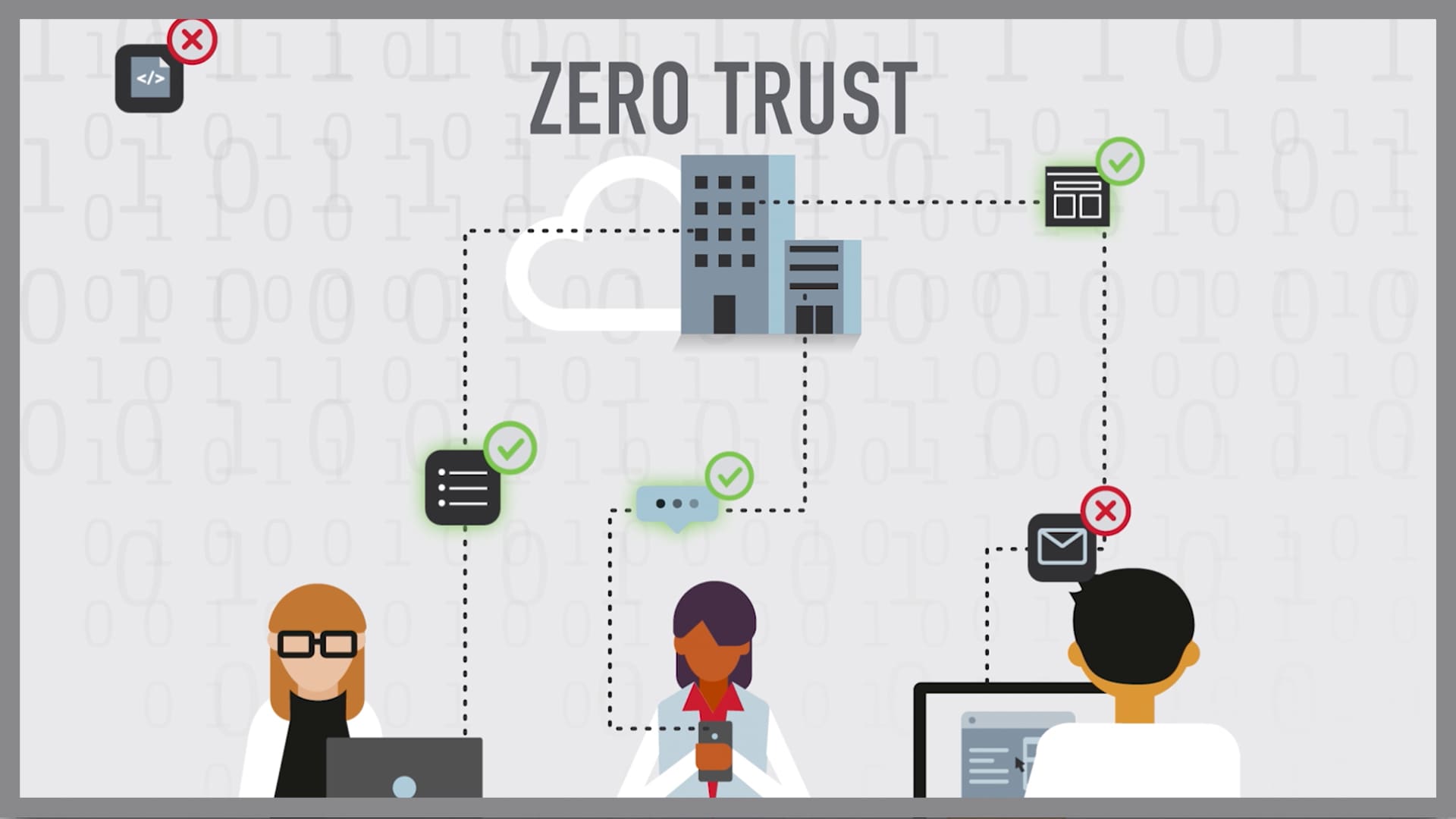
Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices applications and data
Discover the value of grasping What Is Zero Trust Framework in the context of language growth. We'll go over just how efficiency in What Is Zero Trust Framework lays the structure for improved analysis, writing, and total language abilities. Explore the broader effect of What Is Zero Trust Framework on efficient interaction.
Zero Is The New Hero Never Trust Always Verify Edafio
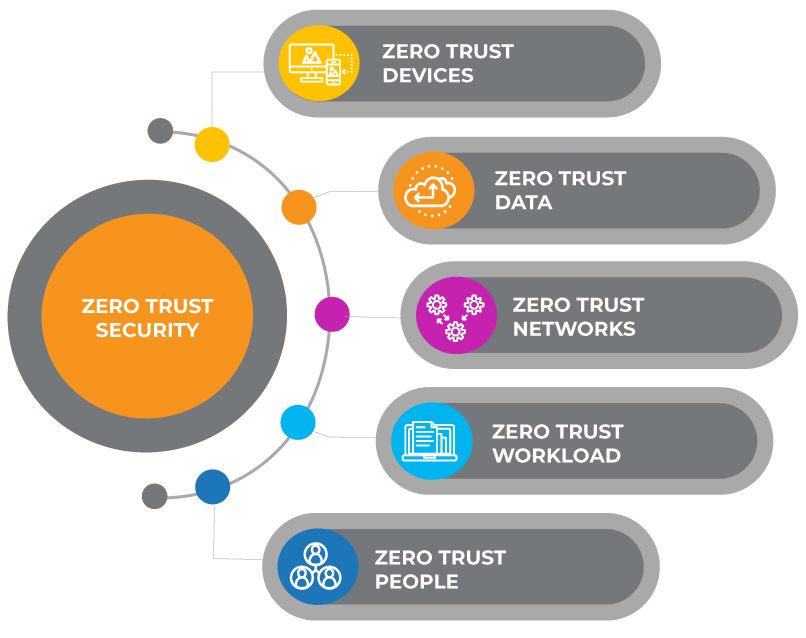
Zero Is The New Hero Never Trust Always Verify Edafio
Zero Trust is a modern security strategy based on the principle never trust always verify Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an open network
Learning does not have to be dull. In this area, discover a variety of appealing activities customized to What Is Zero Trust Framework learners of every ages. From interactive games to creative workouts, these activities are made to make What Is Zero Trust Framework both enjoyable and educational.
Why You Need 6 Layers Of Zero Trust Control

Why You Need 6 Layers Of Zero Trust Control
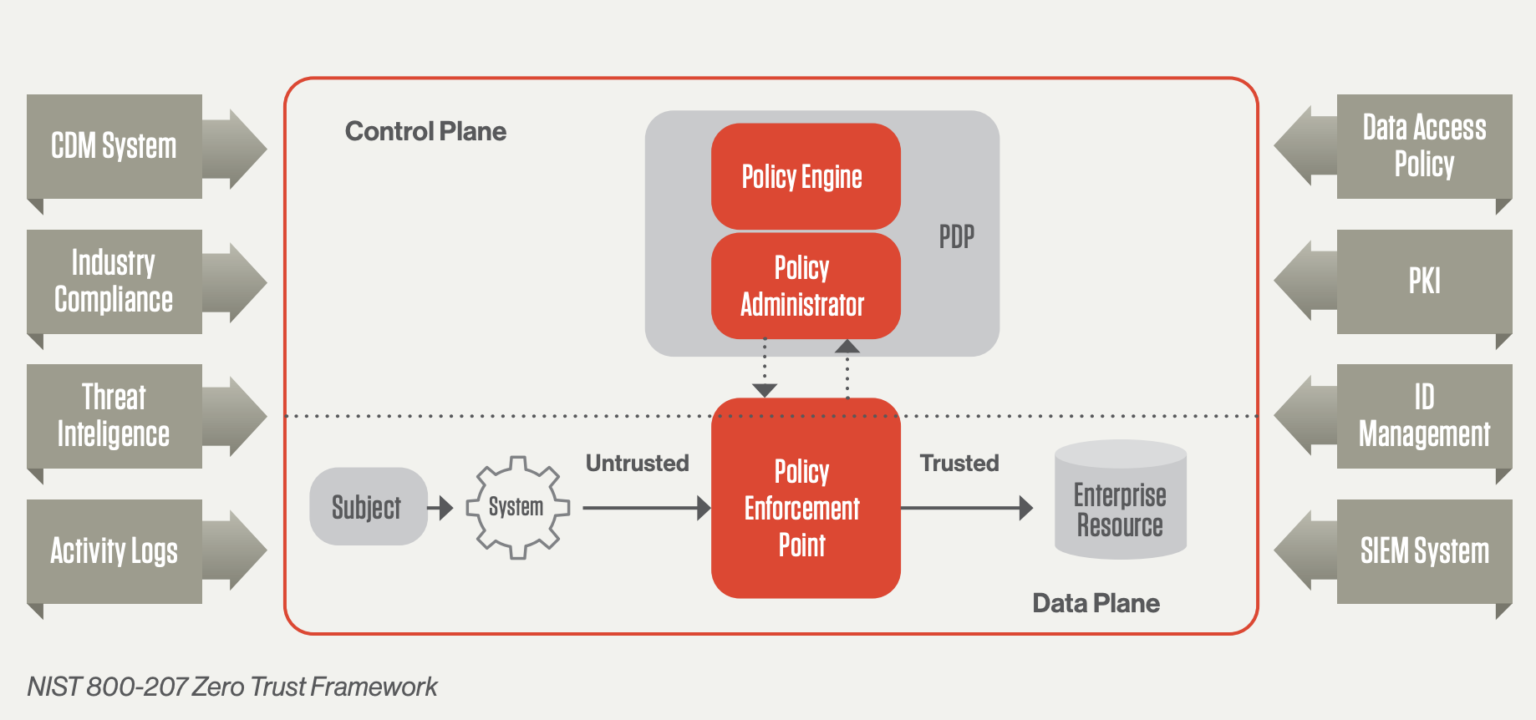
Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows
Accessibility our specifically curated collection of printable worksheets focused on What Is Zero Trust Framework These worksheets accommodate various skill levels, ensuring a personalized learning experience. Download, print, and take pleasure in hands-on tasks that strengthen What Is Zero Trust Framework skills in an effective and pleasurable way.
5 Key Principles Of The NIST Zero Trust Architecture Instasafe Blog

5 Key Principles Of The NIST Zero Trust Architecture Instasafe Blog
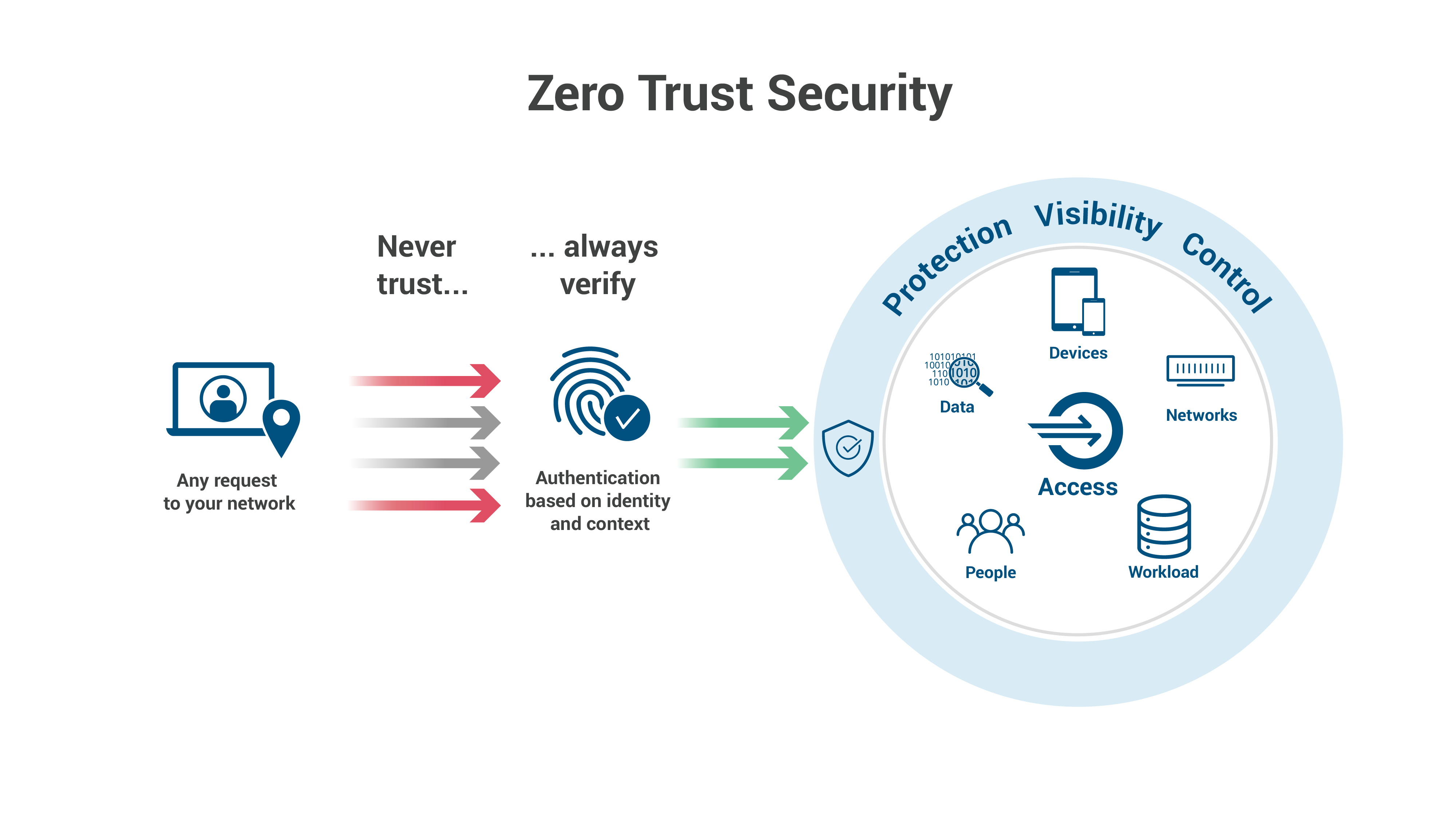
Zero Trust is a framework for securing infrastructure and data for today s modern digital transformation It uniquely addresses the modern challenges of today s business including securing remote workers hybrid cloud environments and ransomware threats
Whether you're an instructor searching for reliable strategies or a student looking for self-guided techniques, this section supplies functional suggestions for grasping What Is Zero Trust Framework. Gain from the experience and insights of instructors that concentrate on What Is Zero Trust Framework education.
Connect with like-minded individuals who share a passion for What Is Zero Trust Framework. Our neighborhood is a room for instructors, moms and dads, and students to exchange ideas, inquire, and celebrate successes in the trip of understanding the alphabet. Join the conversation and belong of our growing neighborhood.
Here are the What Is Zero Trust Framework

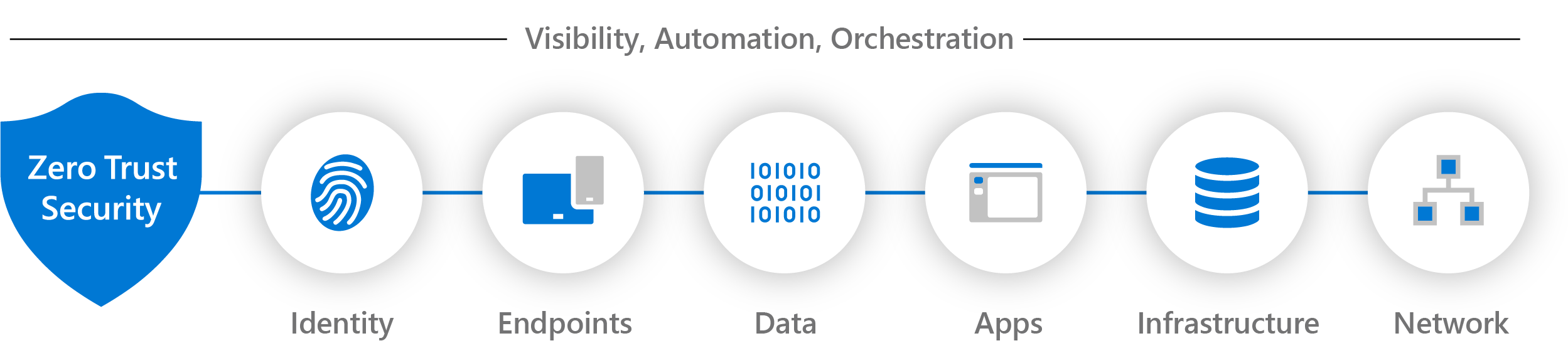
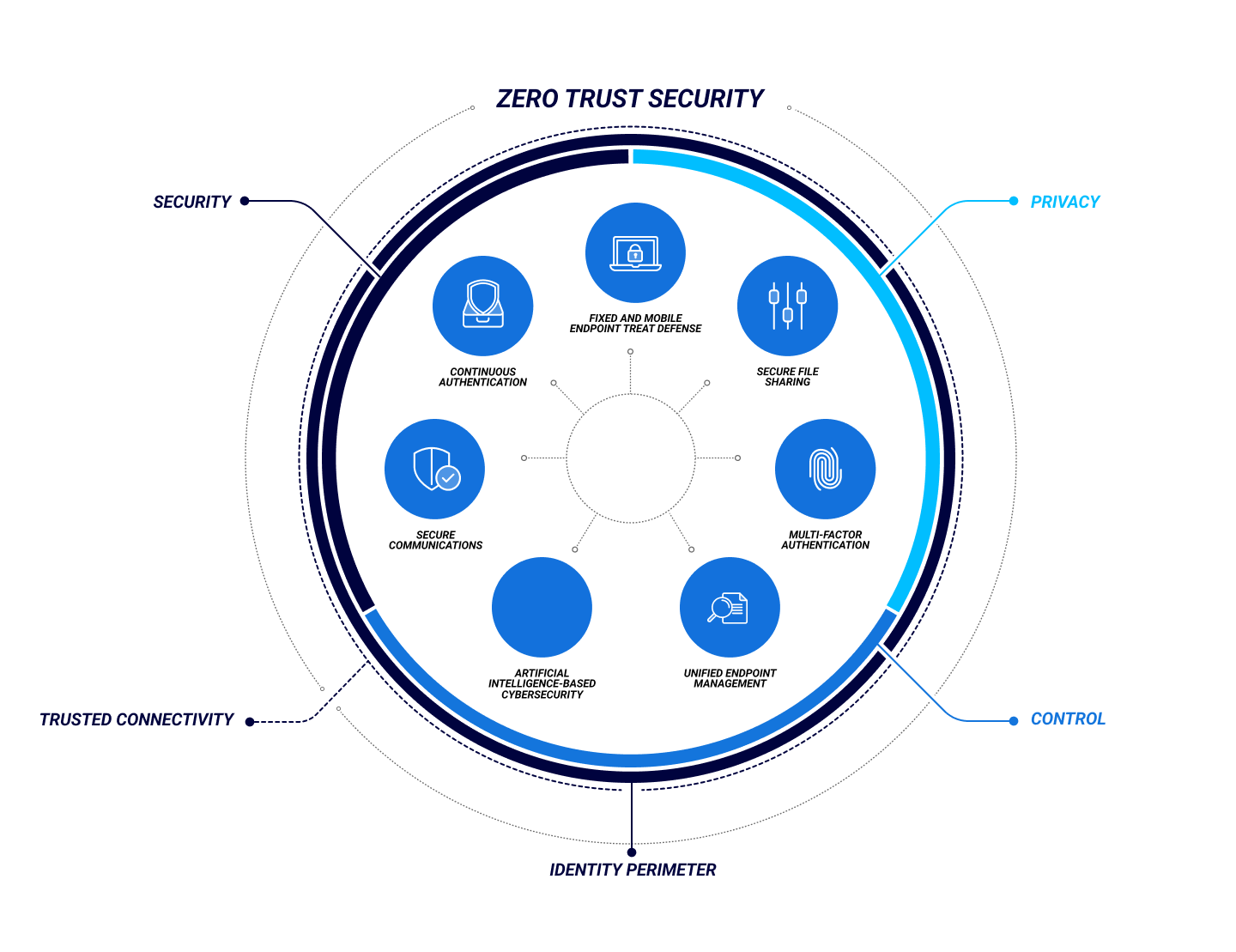
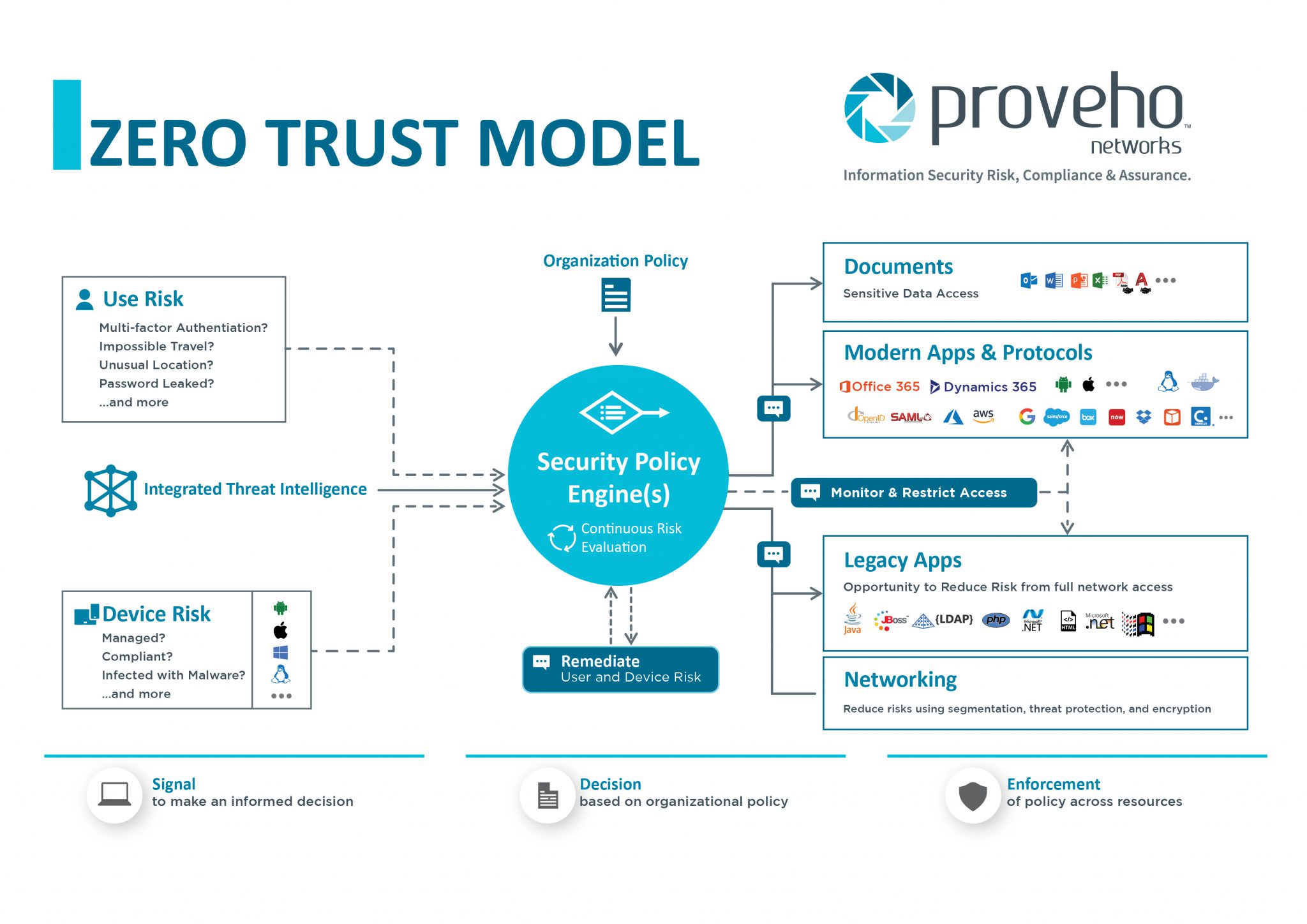


https://www.ibm.com/topics/zero-trust
Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices applications and data

https://www.microsoft.com/en-us/security/business/zero-trust
Zero Trust is a modern security strategy based on the principle never trust always verify Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an open network
Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices applications and data
Zero Trust is a modern security strategy based on the principle never trust always verify Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an open network

Zero trust model 1 png Microsoft 365 Blog

What Is Zero Trust Security

What Is Zero Trust Zero Trust Security Model Akamai

What Is Zero Trust Security Principles Of The Zero Trust Model
Microsoft Zero Trust Architecture Diagram
Forrester Zero Trust Model Images And Photos Finder

Forrester Zero Trust Model Images And Photos Finder

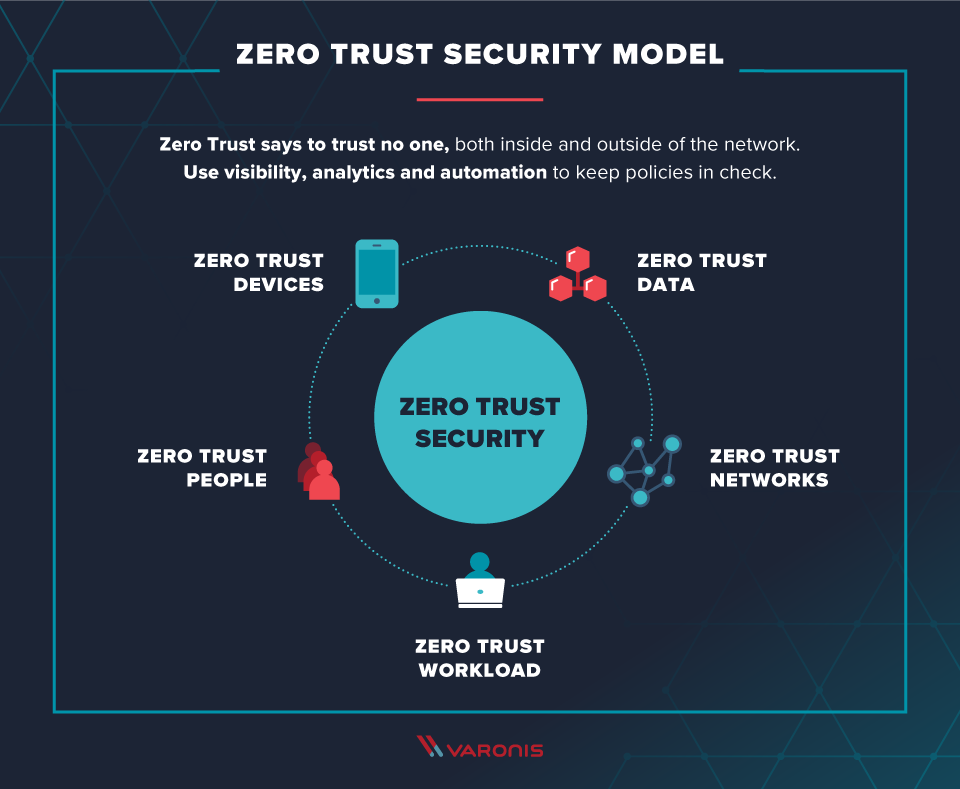
Cybersecurity Journey To Zero Trust 1 VMware