Welcome to PrintableAlphabet.net, your best resource for all things associated with Zero Trust Explained In this thorough overview, we'll look into the intricacies of Zero Trust Explained, offering beneficial insights, engaging activities, and printable worksheets to enhance your learning experience.
Understanding Zero Trust Explained
In this section, we'll check out the fundamental principles of Zero Trust Explained. Whether you're an instructor, parent, or student, obtaining a solid understanding of Zero Trust Explained is crucial for effective language acquisition. Anticipate insights, ideas, and real-world applications to make Zero Trust Explained revived.
Zero Trust El Modelo De Ciberseguridad Que Est Cambiando El Paradigma

Zero Trust Explained
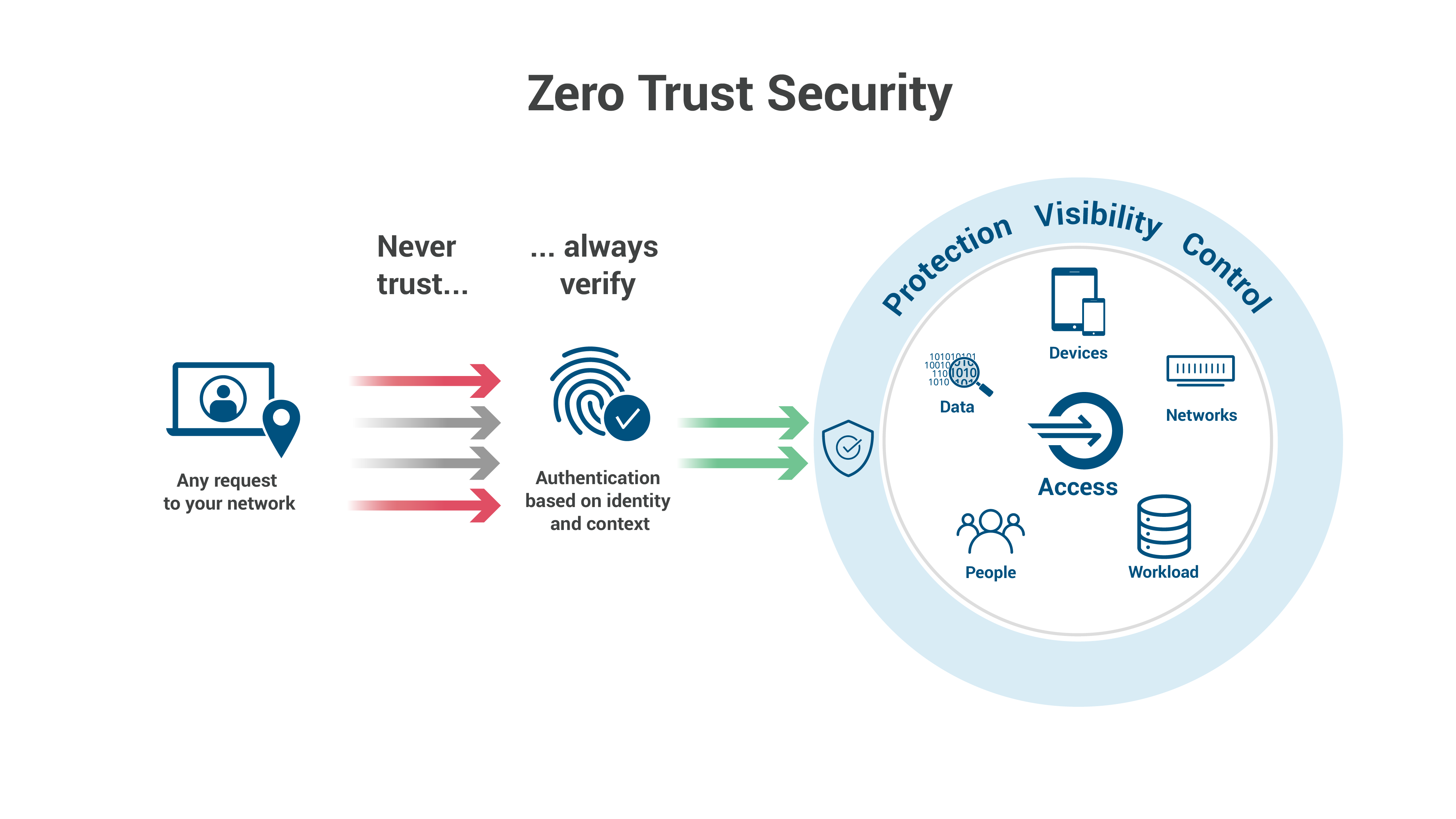
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network regardless of whether they are sitting within or outside of the network perimeter
Discover the importance of grasping Zero Trust Explained in the context of language development. We'll talk about exactly how efficiency in Zero Trust Explained lays the foundation for better analysis, creating, and general language skills. Check out the more comprehensive impact of Zero Trust Explained on effective communication.
What Should You Know About Zero Trust Architecture

What Should You Know About Zero Trust Architecture
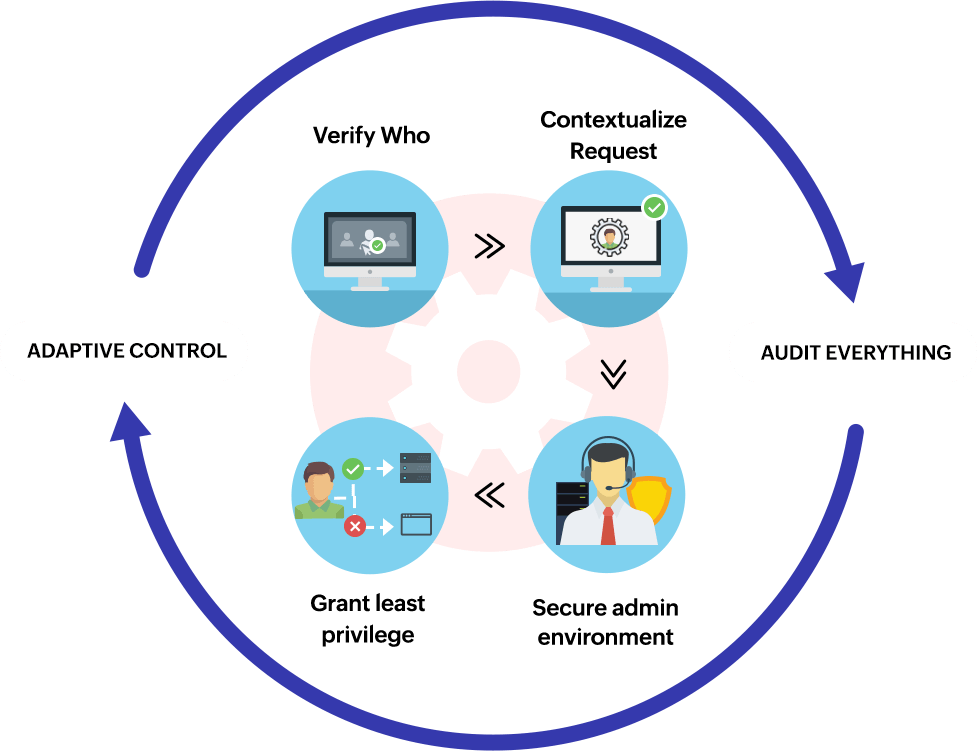
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services
Knowing does not need to be plain. In this section, discover a selection of interesting tasks tailored to Zero Trust Explained learners of all ages. From interactive video games to imaginative exercises, these activities are created to make Zero Trust Explained both enjoyable and academic.
Zero Trust Network Model My XXX Hot Girl
Zero Trust Network Model My XXX Hot Girl
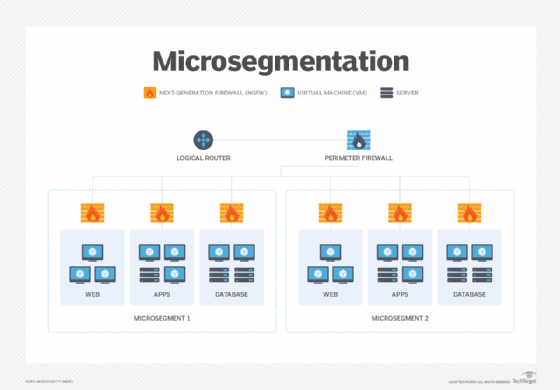
The zero trust security model also zero trust architecture ZTA and perimeterless security describes an approach to the strategy design and implementation of IT systems
Gain access to our specially curated collection of printable worksheets concentrated on Zero Trust Explained These worksheets deal with different skill degrees, making sure a tailored discovering experience. Download and install, print, and delight in hands-on activities that strengthen Zero Trust Explained abilities in a reliable and delightful way.
Zero Trust Security

Zero Trust Security
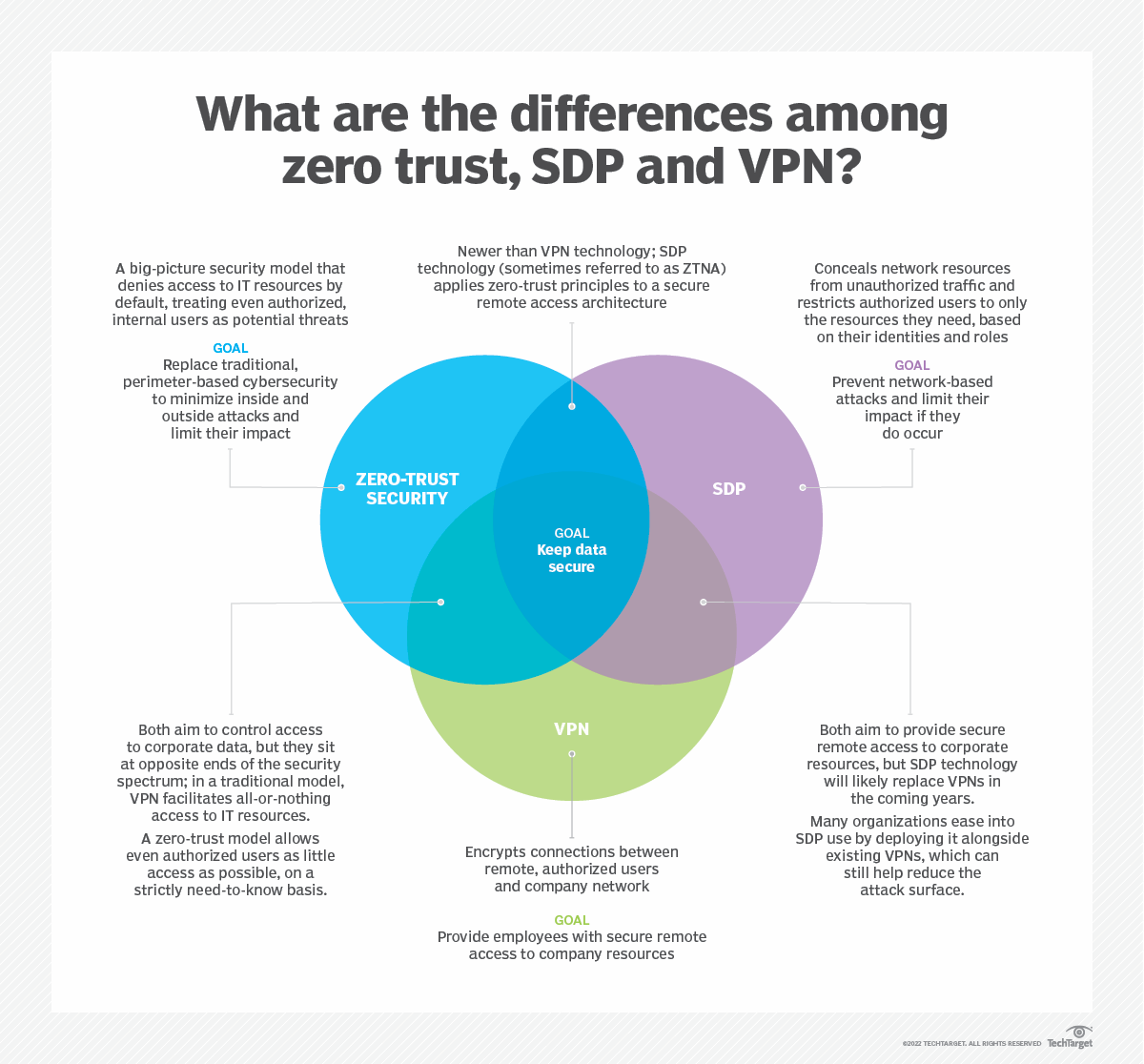
Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices applications and data
Whether you're an educator looking for efficient methods or a learner looking for self-guided strategies, this area supplies useful suggestions for grasping Zero Trust Explained. Take advantage of the experience and insights of teachers who concentrate on Zero Trust Explained education and learning.
Connect with similar people that share an enthusiasm for Zero Trust Explained. Our community is a room for teachers, moms and dads, and learners to trade ideas, consult, and celebrate successes in the trip of mastering the alphabet. Sign up with the discussion and be a part of our growing community.
Download Zero Trust Explained





https://www.cloudflare.com/.../what-is-zero-trust
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network regardless of whether they are sitting within or outside of the network perimeter

https://learn.microsoft.com/.../zero-trust-overview
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network regardless of whether they are sitting within or outside of the network perimeter
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services

Zero Trust Security Explained Zero Trust Components Implementation

Zero Trust Security Explained MSSP Alert

What Is Zero Trust And How Does It Work

Zero Trust Security Architecture
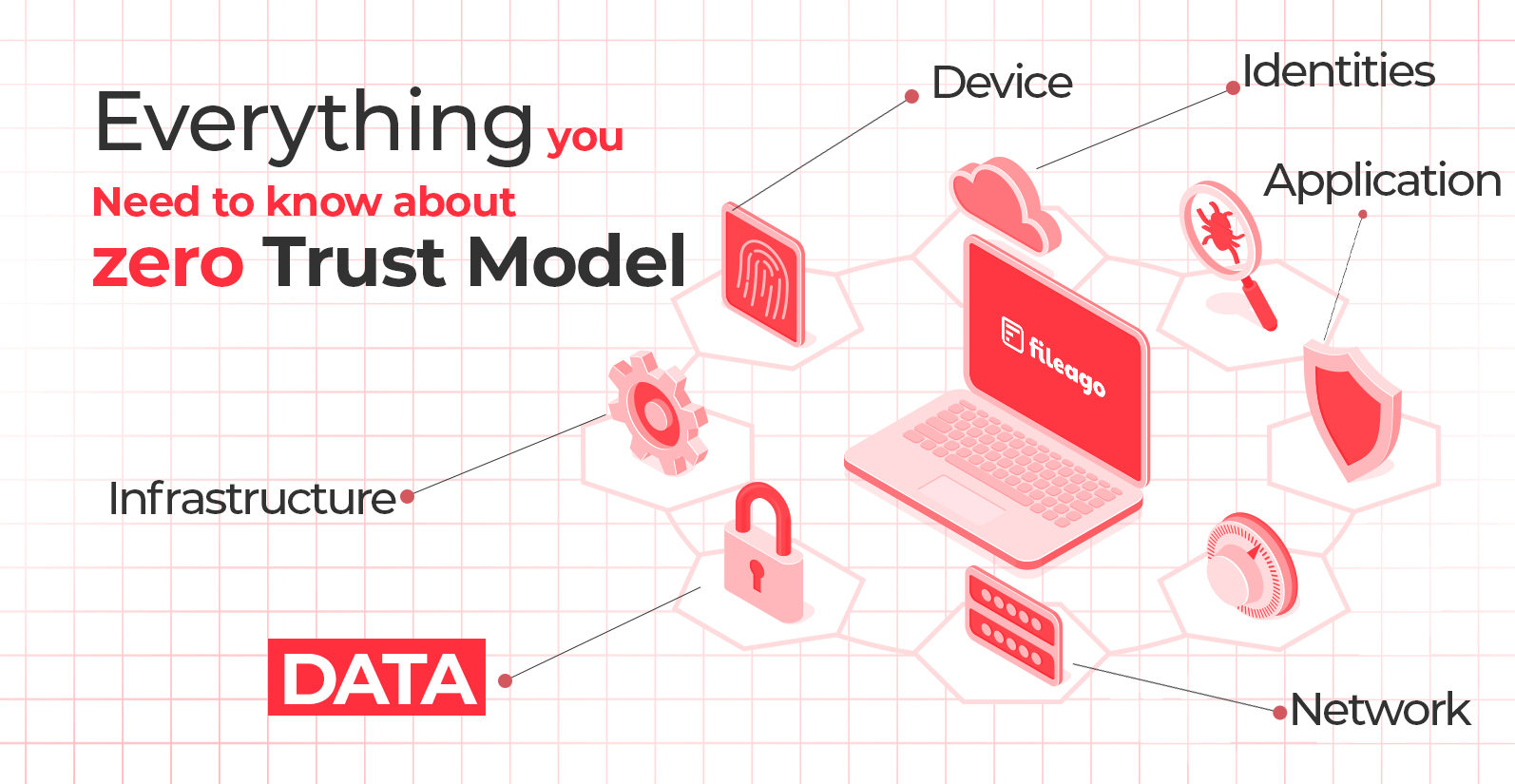
Everything You Need To Know About Zero Trust Model FileAgo

Zero Trust Security Explained ImmuniWeb

Zero Trust Security Explained ImmuniWeb

7 Tenets Of zero Trust Explained CSO Online