Welcome to PrintableAlphabet.net, your go-to source for all points related to What Is Zero Trust In this thorough overview, we'll delve into the intricacies of What Is Zero Trust, supplying valuable insights, engaging tasks, and printable worksheets to improve your knowing experience.
Recognizing What Is Zero Trust
In this section, we'll check out the fundamental ideas of What Is Zero Trust. Whether you're an instructor, moms and dad, or student, acquiring a solid understanding of What Is Zero Trust is vital for effective language procurement. Anticipate insights, ideas, and real-world applications to make What Is Zero Trust come to life.
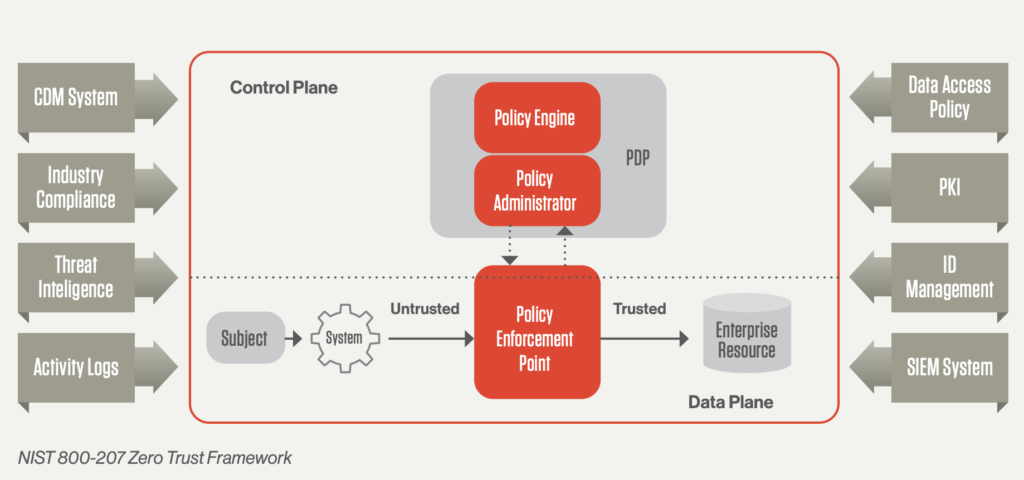
Acceso A La Red De Cero Confianza ZTNA Una Gu a Completa
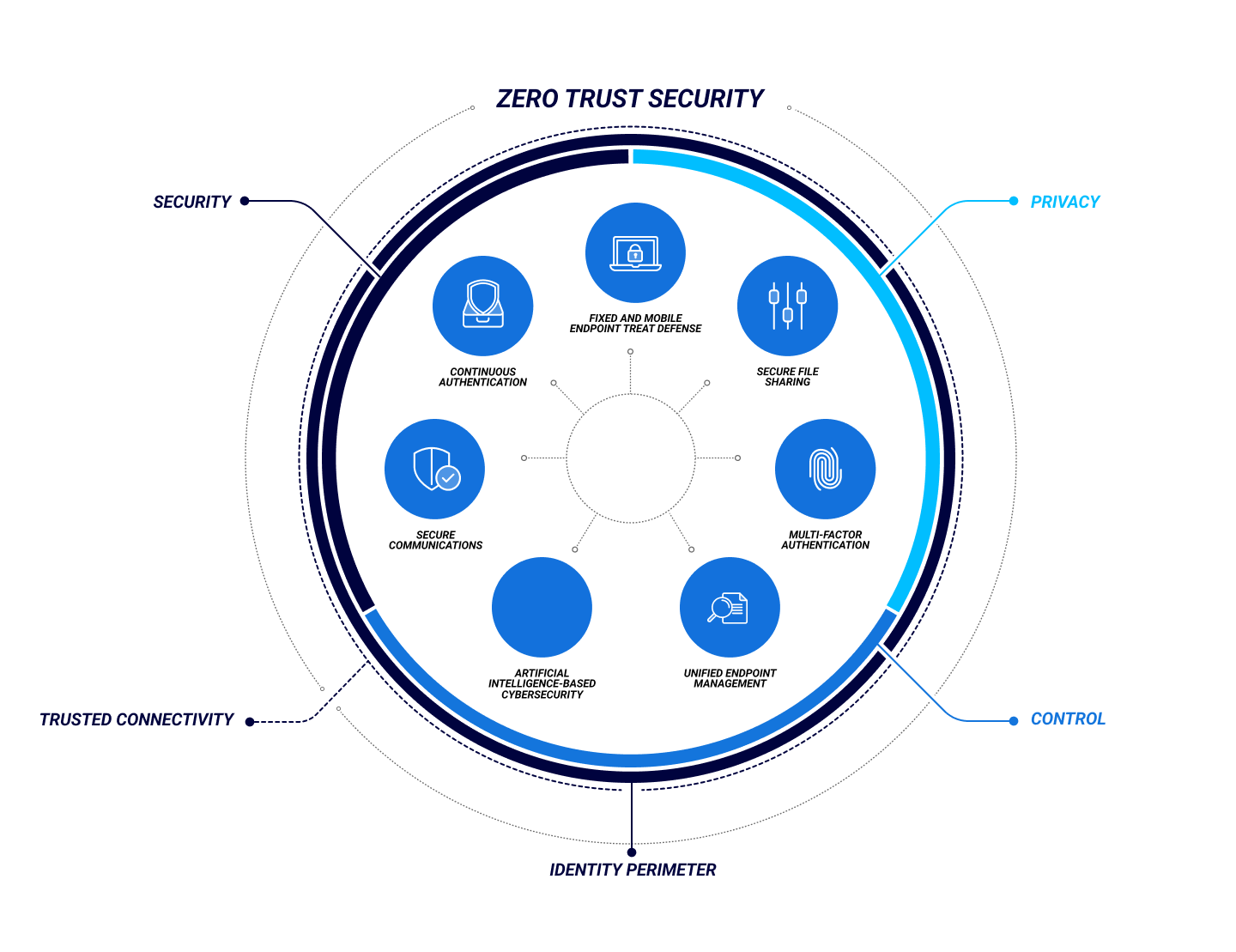
What Is Zero Trust
CrowdStrike s Zero Trust solution has the industry s only frictionless approach to Zero Trust through Security for the most critical areas of enterprise risk to stop breaches in real time for any endpoint and cloud Hyper accurate detections and automated protection ensuring a FRICTIONLESS ZERO
Discover the relevance of grasping What Is Zero Trust in the context of language advancement. We'll review how efficiency in What Is Zero Trust lays the foundation for enhanced analysis, composing, and total language abilities. Check out the wider influence of What Is Zero Trust on effective communication.
What Is Zero Trust And Why Is It So Important

What Is Zero Trust And Why Is It So Important
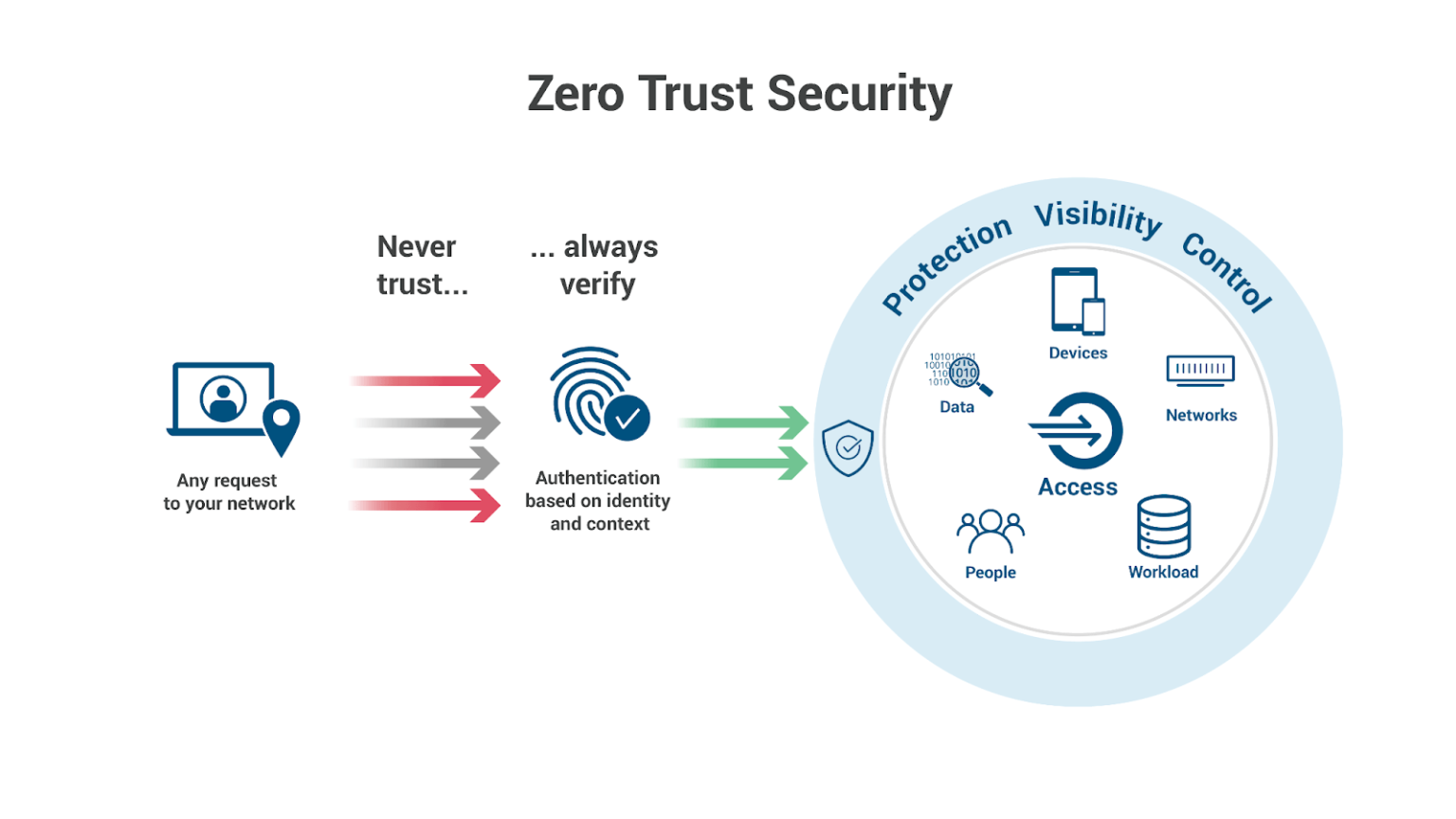
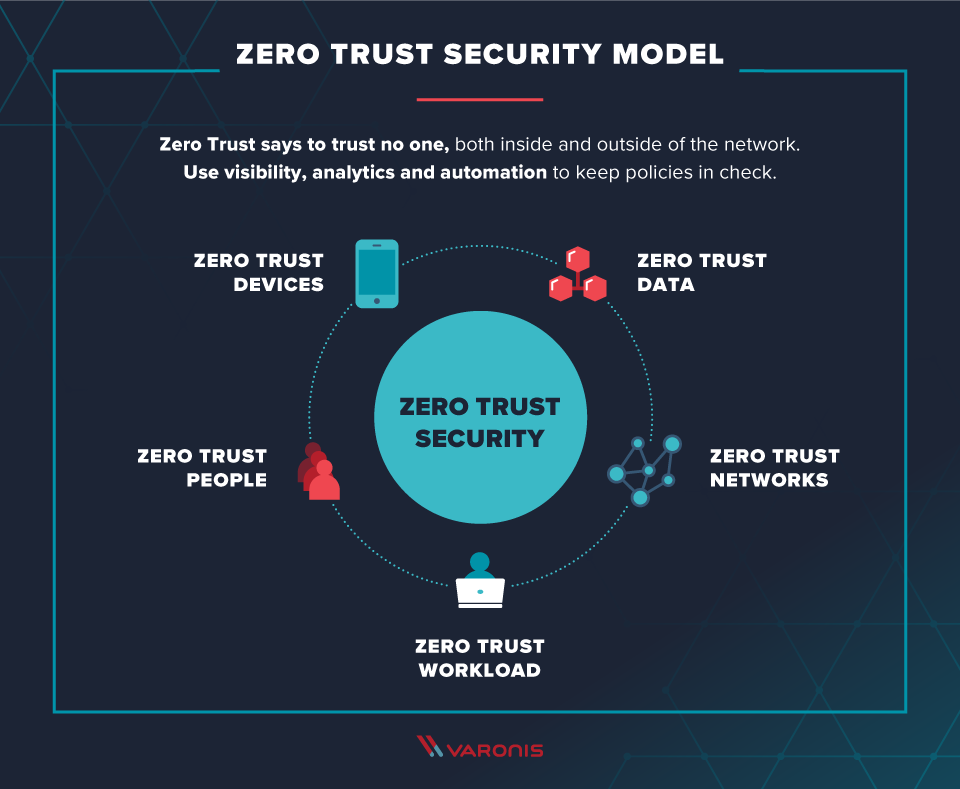
Zero Trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network This added layer of security has been shown to prevent data breaches
Learning does not have to be boring. In this section, locate a selection of engaging activities customized to What Is Zero Trust learners of every ages. From interactive games to innovative exercises, these activities are developed to make What Is Zero Trust both enjoyable and instructional.
What Is Zero Trust Zero Trust Security Model Akamai
What Is Zero Trust Zero Trust Security Model Akamai
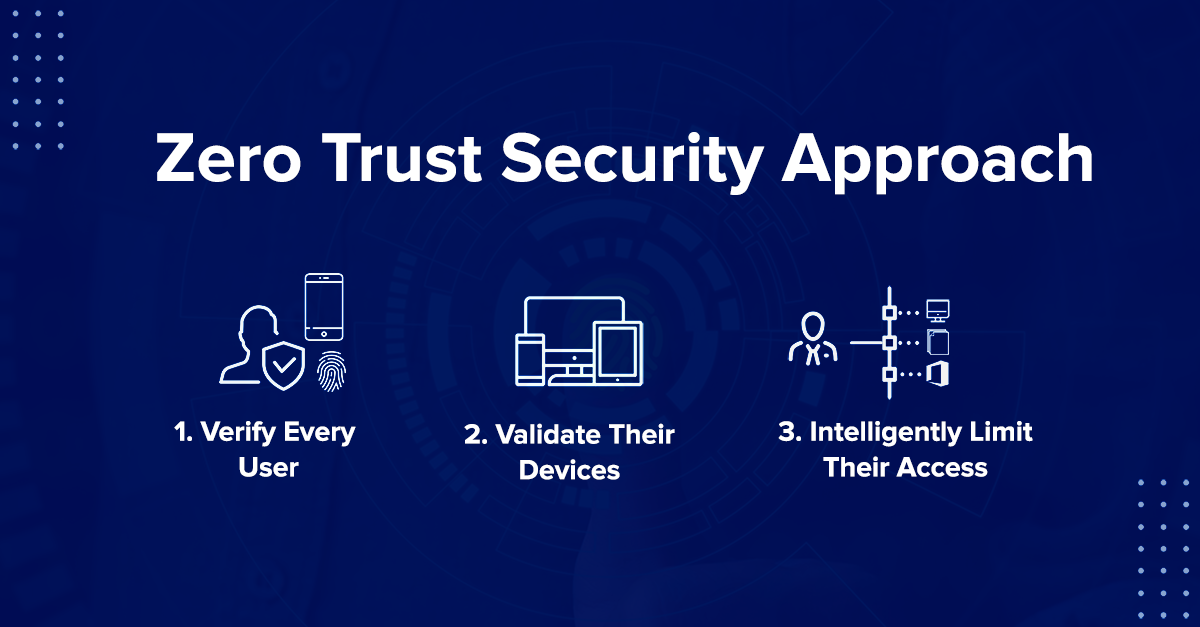
Frequently asked questions What is Zero Trust Zero trust is a modern security strategy based on the principle never trust always verify Instead What are the main pillars of Zero Trust The three main pillars of Zero Trust are Verify explicitly always Why do organizations need Zero Trust
Gain access to our particularly curated collection of printable worksheets focused on What Is Zero Trust These worksheets cater to various ability degrees, ensuring a personalized understanding experience. Download, print, and enjoy hands-on tasks that enhance What Is Zero Trust abilities in an efficient and satisfying means.
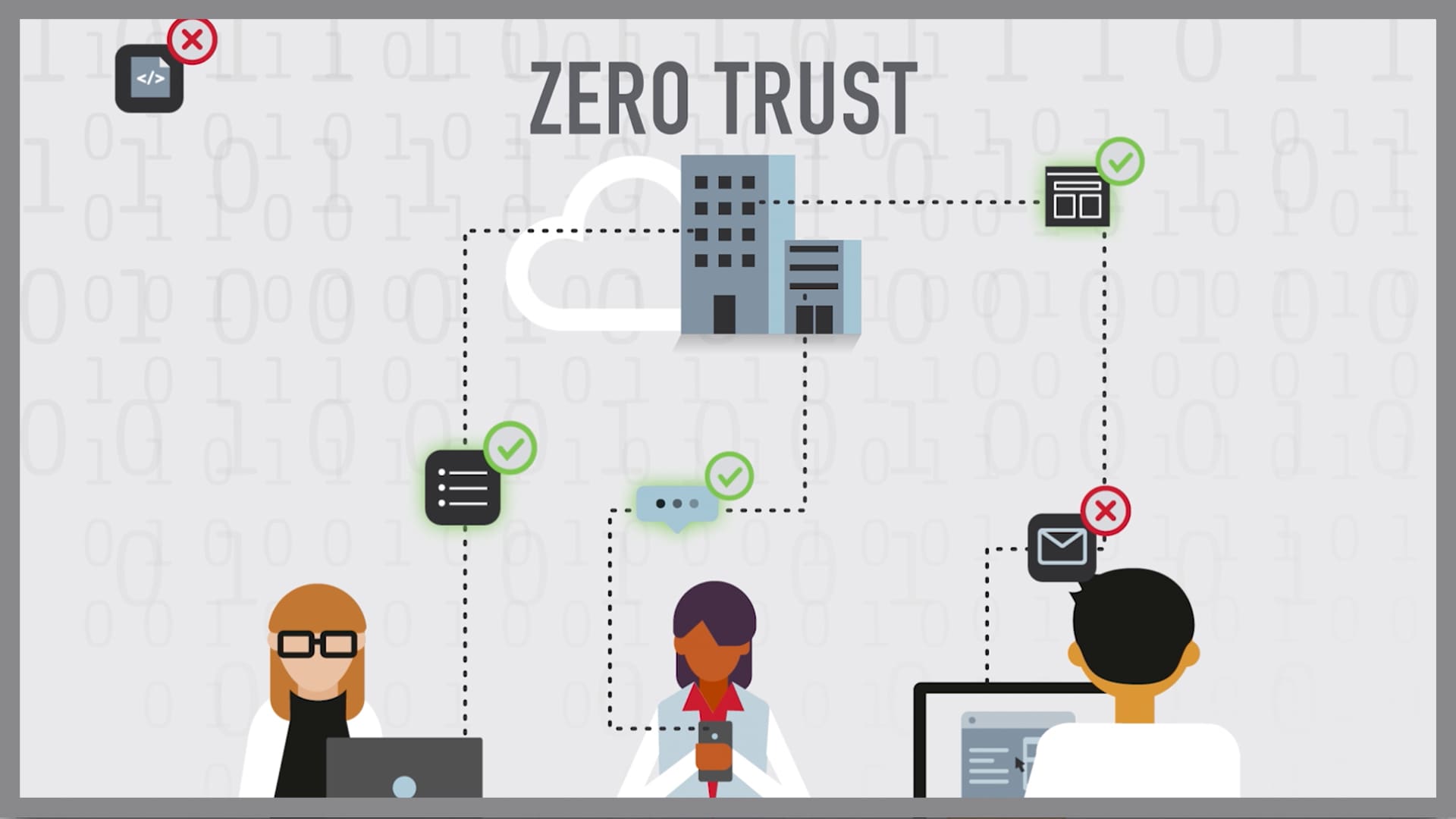
Zero Trust The Road Towards More Effective Security QuickLaunch
Zero Trust The Road Towards More Effective Security QuickLaunch
To make a zero trust model work adopters must Make an organization wide commitment Catalog all IT and data assets and assign access rights based on roles Lock down some common vulnerabilities Classify data for a data centric approach link resides outside ibm Segment networks to prevent
Whether you're an instructor looking for reliable approaches or a student looking for self-guided techniques, this area offers practical pointers for mastering What Is Zero Trust. Gain from the experience and understandings of instructors who concentrate on What Is Zero Trust education and learning.
Connect with like-minded people that share a passion for What Is Zero Trust. Our neighborhood is a space for teachers, parents, and students to trade concepts, inquire, and commemorate successes in the journey of mastering the alphabet. Sign up with the conversation and belong of our growing community.
Download What Is Zero Trust




https://www.crowdstrike.com/cybersecurity-101/zero-trust-security
CrowdStrike s Zero Trust solution has the industry s only frictionless approach to Zero Trust through Security for the most critical areas of enterprise risk to stop breaches in real time for any endpoint and cloud Hyper accurate detections and automated protection ensuring a FRICTIONLESS ZERO

https://www.cloudflare.com/learning/security/glossary/what-is-zero-trust
Zero Trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network This added layer of security has been shown to prevent data breaches
CrowdStrike s Zero Trust solution has the industry s only frictionless approach to Zero Trust through Security for the most critical areas of enterprise risk to stop breaches in real time for any endpoint and cloud Hyper accurate detections and automated protection ensuring a FRICTIONLESS ZERO
Zero Trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network This added layer of security has been shown to prevent data breaches

Zero Trust

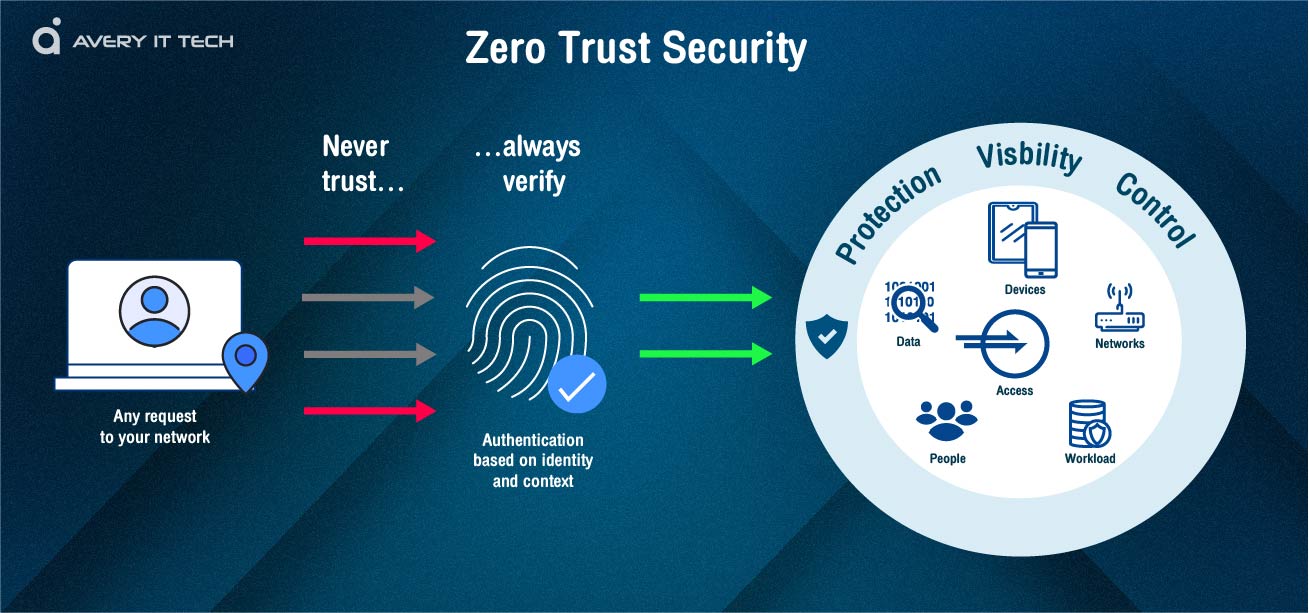
Zero Trust Network Access Concept Averyittech

Zero Trust For Government Networks 6 Steps You Need To Know Cisco Blogs

Pros And Cons Of The Zero Trust Model
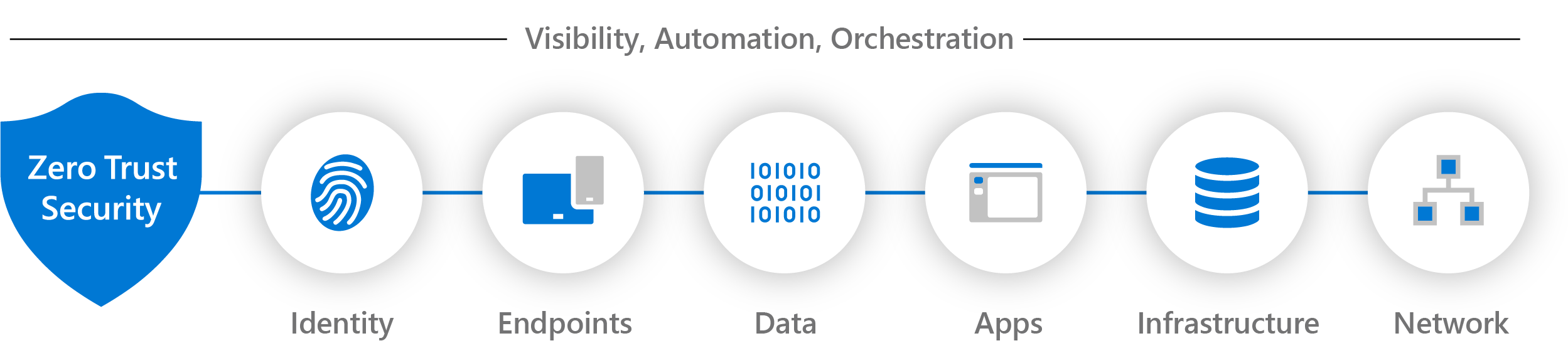
Apa Itu Zero Trust Microsoft Learn

Zero Trust Security Architecture Overview Images And Photos Finder

Zero Trust Security Architecture Overview Images And Photos Finder

Overhauling Zero Trust How To Enforce The Security You Need